Token Security’s MCP Server Discovery Capability Uncovers Hidden AI Servers and Secrets

As enterprises rapidly adopt AI-driven tools, a new category of shadow IT is emerging: Model Context Proxy (MCP) servers. MCP is an open standard introduced by Anthropic that allows AI agents, such as coding copilots, LLMs, and autonomous agents, replacing fragmented integrations with a single protocol to connect to external data sources and tools via natural language. These lightweight MCP servers can browse files, query databases, create tickets, delete CRM records, call APIs, and control applications, enabling powerful workflows.
But in practice, MCP servers are often created without the knowledge of enterprise security teams. They are spun up as makeshift projects with access to personal and confidential access using OAuth and long-term credentials. AI coding assistants and endpoint AI tools may silently connect to MCP servers on developer machines or cloud instances, outside of IT oversight. Each of these servers operates as a local or remote service with access to sensitive systems, yet they typically aren’t inventoried, monitored, or governed by existing security controls. For security teams, this creates a rapidly growing blind spot embedded directly into the enterprise AI stack.
Why Traditional Security Tools Miss MCP Servers
MCP servers evade detection because they usually authenticate using personal user credentials, meaning it's hard to differentiate between user initiated actions and agentic actions via an MCP server. Security teams do not see MCP servers as an active threat, but they should be considered potential vulnerabilities because of their access. They appear as benign helper processes rather than standalone infrastructure. Traditional endpoint, identity, and network tools were never designed to monitor AI-driven agent processes, leaving enterprises with privileged services running invisibly on endpoints.
The risks are significant. MCP servers frequently store hardcoded secrets (API keys, tokens, and credentials) inside configuration files or environment variables. For example, an MCP server connecting an AI assistant to GitHub may store a personal access token in plaintext. Any process or AI agent that can read the config can extract those credentials. Even with proper OAuth, MCP servers act on the behalf of their users but without guidance and approval which can lead to unwanted and risky results.
This risk is not theoretical. AI coding tools are already leaking sensitive configuration files and secrets, sometimes transmitting them externally. Researchers have demonstrated prompt-injection attacks that trick AI assistants into exfiltrating secrets via covert channels such as DNS queries. In other cases, MCP servers run with full user privileges, meaning they can send data anywhere on the internet using the user’s credentials.
Beyond secret exposure, MCP servers introduce unmonitored connections to critical business systems (i.e. AWS, Salesforce, Snowflake, and more) and data paths. By design, they initiate outbound connections to external services. If compromised or misconfigured, they can quietly exfiltrate data or provide backdoor access to internal files without generating logs or alerts. These shadow AI actions often go unrecorded, breaking Zero Trust assumptions and making forensic analysis nearly impossible.
The result is a dangerous visibility gap: hidden services, embedded secrets, and untracked connections operating in plain sight. For attackers, MCP servers are an ideal hiding place. For defenders, they represent a growing compliance and security liability.
Introducing Token Security’s MCP Server Discovery Capabilities
To address this challenge, Token Security is launching its MCP Server Discovery capabilities as part of our continuous discovery engine. This capability is designed to automatically find, inventory, and analyze MCP servers and AI agents operating across the enterprise to bring hidden AI infrastructure back under security control.
Our MCP Server Discovery capability integrates deeply with endpoint and identity ecosystems without the need for agents, including CrowdStrike and others. Token Security continuously scans the environment and conducts forensic analysis for MCP servers and agentic AI processes. The Token Security platform analyzes CrowdStrike logs for IDEs and Claude Code instances, and uses this data to pinpoint what MCPs they're communicating with. When an MCP server appears anywhere in the environment, the Token Security platform discovers it in near real time based on the logs.
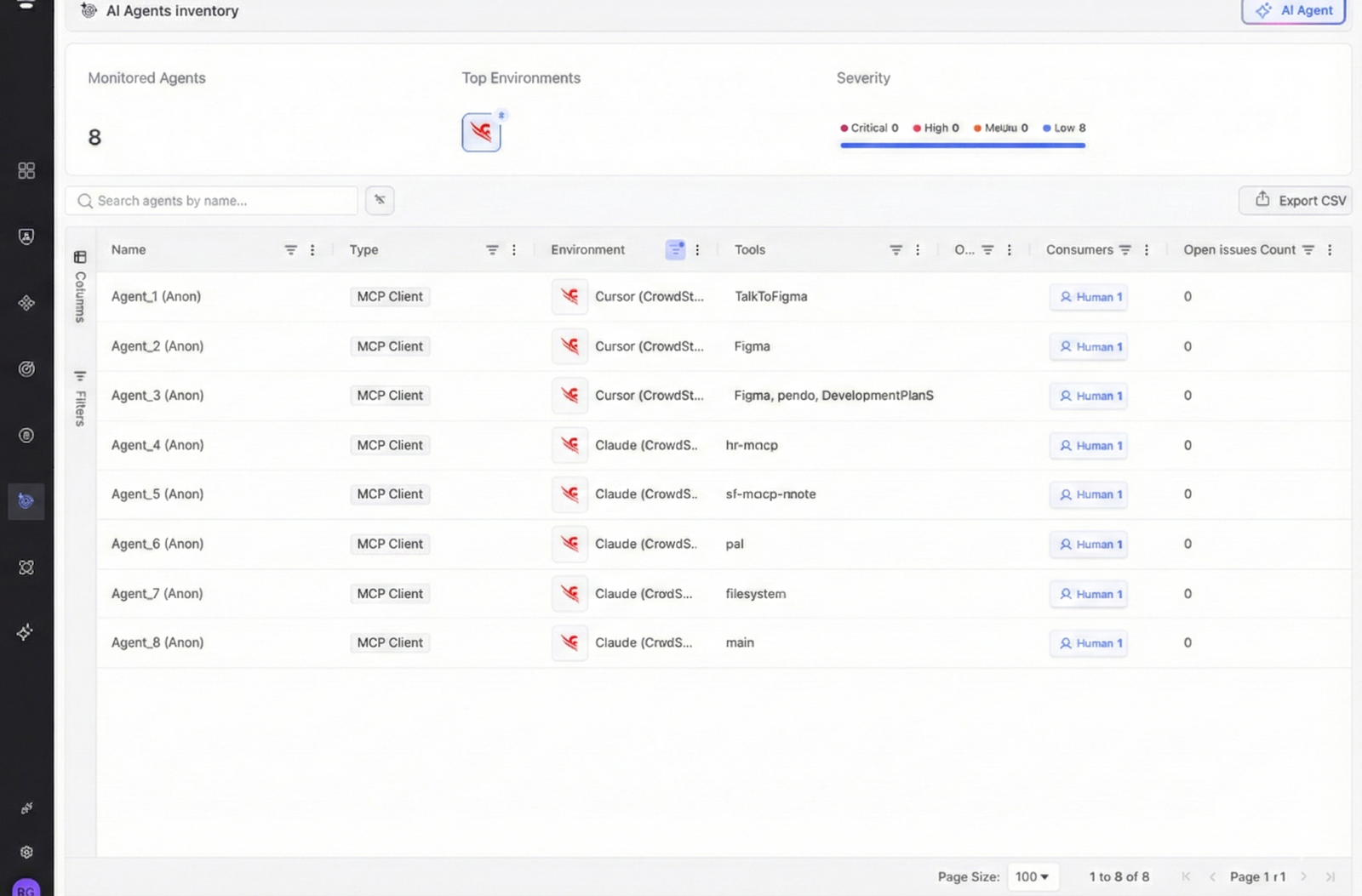
Once detected, Token Security leverages CrowdStrike’s Real Time Response (RTR) to remotely and securely collect MCP configuration files from the endpoint. For example, files such as claude_desktop_config.json or other .mcp.json configs are retrieved automatically, without user disruption. This creates a seamless pipeline from detection to analysis.
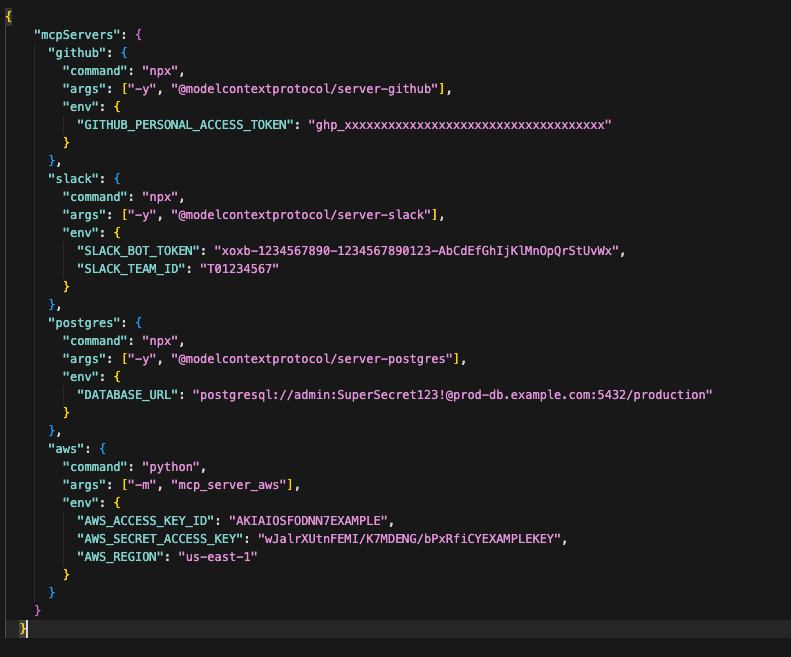
Deep Analysis and Risk Exposure
The Token Security platform analyzes each discovered MCP instance and classifies it based on authentication. This analysis produces a clear, contextual inventory showing where each MCP server runs, what systems or data it can access, and how it is connected.
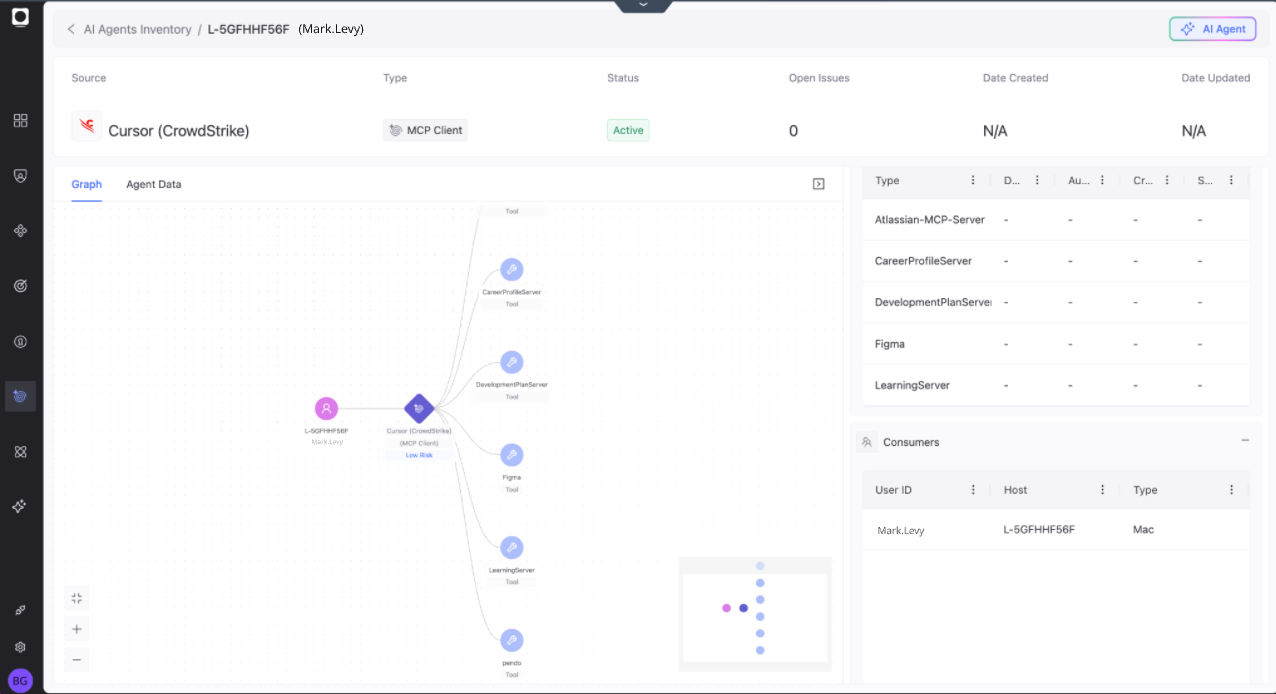
Critically, Token Security scans all collected configuration files to identify the access and risky settings. Hardcoded secrets (API keys, plaintext tokens, and more) are identified and correlated to the identity, with sensitive values safely redacted. The platform also flags dangerous configurations, such as overly broad permissions in services that could be exploited.
The result is an actionable inventory of every MCP server: what it is, what it touches, and what risks it introduces.
Gaining Control Over Shadow AI
The MCP Server Discovery capability gives security teams visibility into AI infrastructure that was previously invisible. Every MCP server and AI agent is automatically uncovered and cataloged, closing a critical gap in discovery and visibility. Teams can now determine who deployed each AI service, what it’s doing, and whether it complies with policy.
The benefits are immediate. Secret sprawl is reduced as exposed keys and tokens are identified and remediated. Shadow integrations and data paths are illuminated, enabling teams to control or shut down risky connections. And, governance improves without blocking innovation, so developers can continue using AI tools, but those tools are now visible and accountable.
More broadly, our MCP Server Discovery capability aligns AI adoption with Zero Trust principles by ensuring no AI process operates unseen or ungoverned. It reduces attack surface, improves auditability, and supports compliance as organizations increasingly need to account for non-human identities and AI-driven systems.
Conclusion
Token Security’s MCP Server Discovery capability delivers the deep visibility security demand into modern AI environments. By combining continuous endpoint discovery and configuration-level analysis, it exposes hidden AI servers, embedded secrets, and risky connections before they can be exploited.
With MCP Server Discovery, organizations can confidently embrace AI assistants and MCP integrations by turning a hidden security liability into a managed, governed asset.
To see our MCP Server Discovery capability in action, request a demo of the Token Security platform today.
.gif)