The Agentic AI Security Challenge
Organizations are racing to adopt agentic AI to enable innovation, gain a competitive advantage, and realize operational efficiencies. But with rapid adoption comes real risk, and today’s identity and access controls aren’t built for autonomous agents.
Identity Sprawl,
Out of Control
AI agents multiply unchecked, creating unmanaged identities and orphaned accounts with lingering access
Unpredictable AI Behavior, Zero Accountability
Autonomous agents act unpredictably, making it nearly impossible to trace actions and detect anomalies
Over-Privileged Agents, Expanded Attack Surface
Excessive, long-lived permissions leave AI agents dangerously overexposed to compromise
One Breach, Organizational Compromise
A single compromised AI agent can cascade across systems, amplifying damage instantly
Static Secrets, Zero Trust Blind Spots
Unrotated API keys or stale tokens without MFA protection, create exploitable security gaps
Securing Agentic AI at Scale
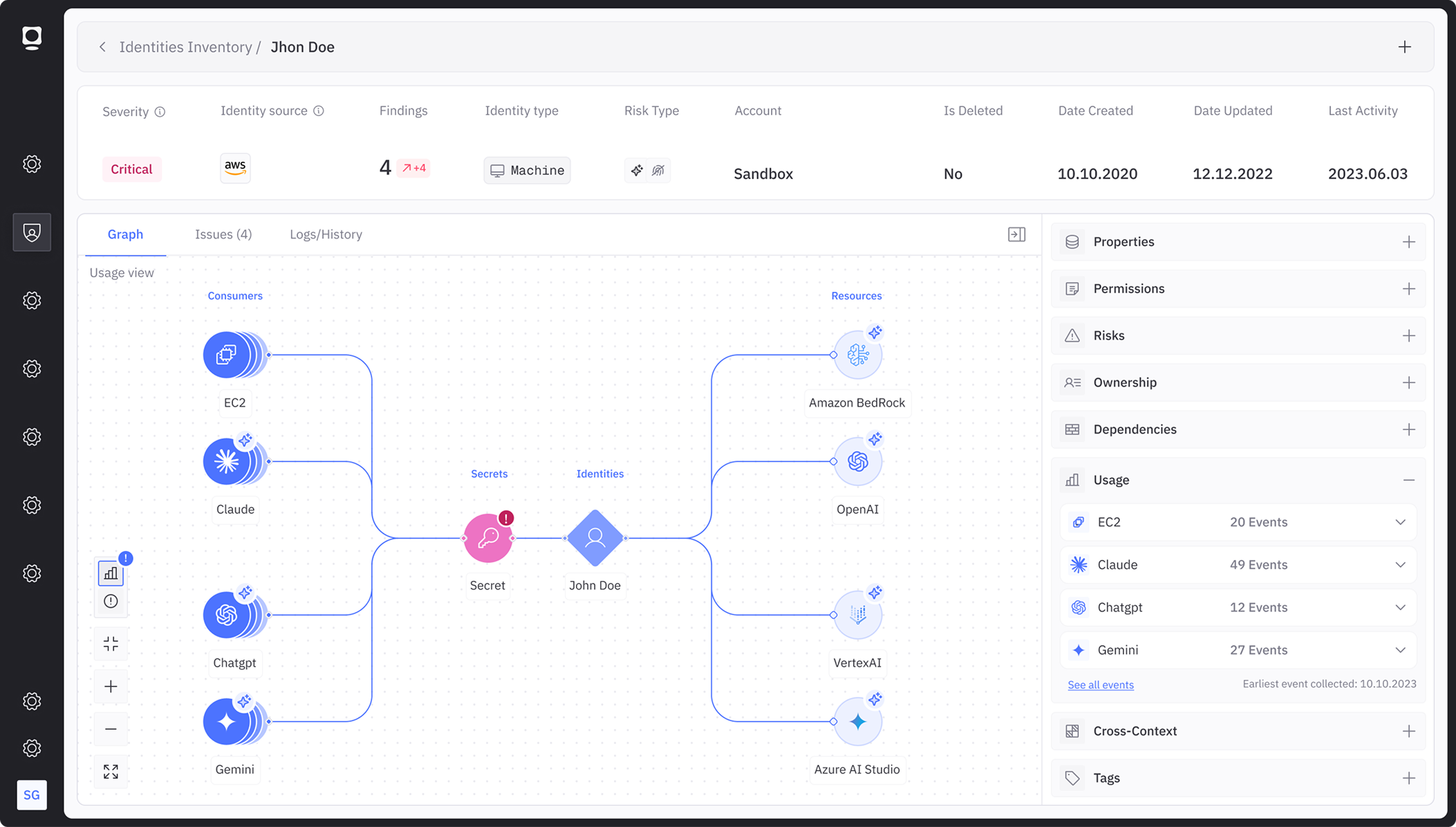
The Token Security Solution
The Token Security platform is purpose-built to secure the identities supporting agentic AI deployments by delivering visibility, control, and governance that enterprises need to secure AI at scale. Key capabilities include:

Discover Hidden AI Agents and MCP Servers
Automatically uncover Shadow AI and MCP servers, giving you complete visibility and eliminating blind spots

Establish AI Agent Ownership and Accountability
Assign ownership, rotate credentials, and retire orphaned agents before they become long-term risks

Enforce AI Agent Access Control and Right-Sizing
Continuously enforce least privilege and just-in-time access, remediating excessive permissions in real time

Ensure Traceability in a Multi-Agent Ecosystem
Log every AI agent action across ecosystems, ensuring compliance and rapid incident investigation
Plug Token Security Into Your AI Stack
Integrate with your existing AI frameworks to get instant visibility and control over every agent. Token Security connects to your managed AI ecosystems, so you don’t just discover shadow AI, you inventory the agents you already run, establish ownership, map their access, and right-size permissions.
Works with your AI frameworks
What Sets Token Security Apart
Token Security is built for organizations that need more than discovery. From AI agent identity hygiene to intelligent remediation, we deliver uncompromising control, so you can trust your AI infrastructure.
Contextual Awareness:
End-to-end AI Agent Lifecycle Control:
Intelligent Remediation at Scale:
Integrated Privilege Governance:
Real-Time Threat Response:
Ready to See Token Security in Action?
Token Security empowers CISOs and security and identity teams to embrace agentic AI safely and securely without compromising innovation, agility, and compliance.
Request a DemoEnsure Traceability in a Multi-Agent Ecosystem

The challenge
Business impact
Token Security solution
The Challenge
AI agents often act autonomously and invoke other agents, creating complex chains of decisions. Without proper oversight, tracing what happened and why becomes nearly impossible. Traditional logs lack context, leaving security teams unable to reconstruct incidents or demonstrate compliance. When regulators or executives ask, “Who authorized this action?” too often the answer is, “We don’t know.”
Business Impact
Hidden Threats
Rogue or malicious agents can hide behind the complexity of multi-agent interactions.

Incident Response Delays
Without full context, identifying the root cause can take days instead of minutes.

Liability Risks
No records of action and traceability leaves the organization exposed when compromised.

Regulatory Penalties
Insufficient logging is treated as a control failure in audits.
The Token Security Solution
Token Security ensures complete traceability of all AI agent actions across your entire ecosystem, fulfilling the often-missing audit layer in autonomous operations.
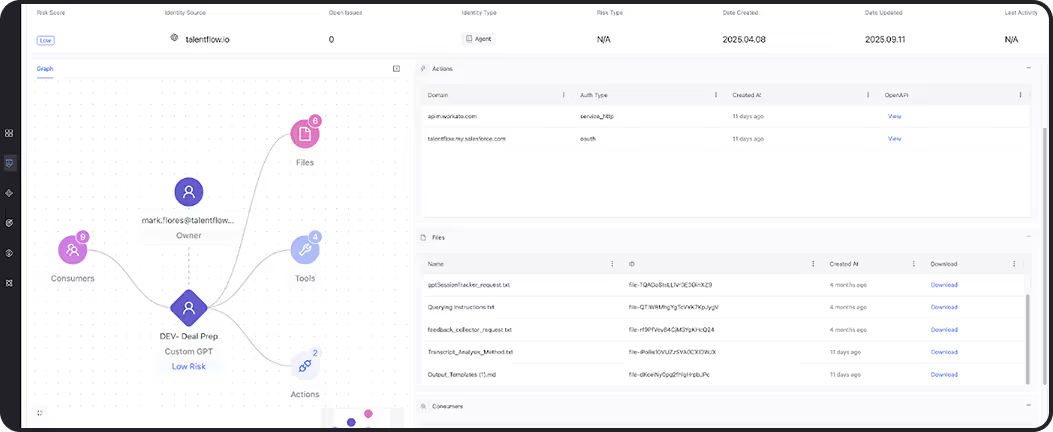
Comprehensive Logging
Every AI action across your ecosystem is captured, structured, and centralized
Contextual Correlation
Multi-agent sequences are stitched together into clear timelines.
Real-Time Alerts
Suspicious agent activity triggers immediate detection and response.
Audit-Ready Records
Immutable logs meet retention and compliance requirements.
With Token Security, every action is logged, every identity is tied to an owner, and every decision can be traced back. In line with Zero Trust, it treats every AI action as “guilty until proven innocent” that is verified by an indelible record, so even in a sprawling, multi-agent environment, nothing operates without oversight and accountability
Business Value

Accelerate incident response with forensic-grade audit trails

Strengthen trust in AI systems by ensuring full accountability

Gain real-time visibility into even the most complex multi-agent interactions

Prove compliance with clear, immutable logs
.gif)

















