Third-Party NHI Security
Secure the extended enterprise with visibility and control over non-human identities accessed by suppliers, contractors, and partners across your ecosystem.



The Solution
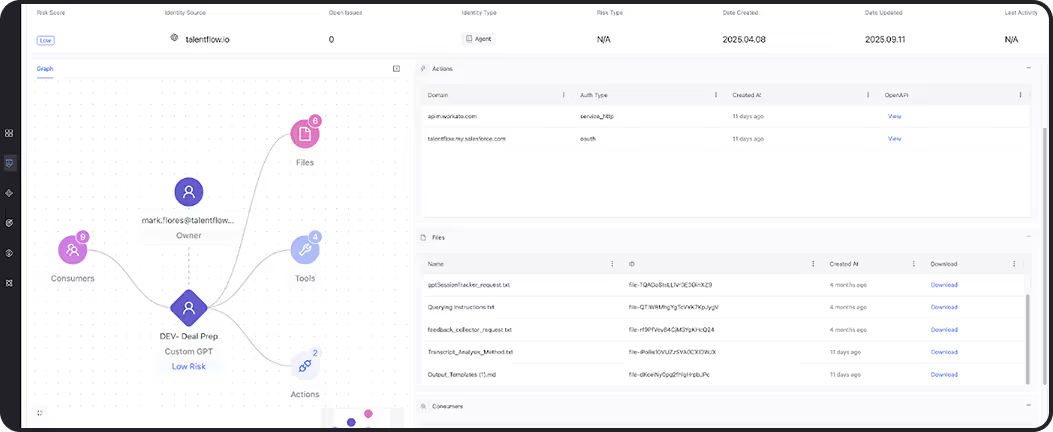
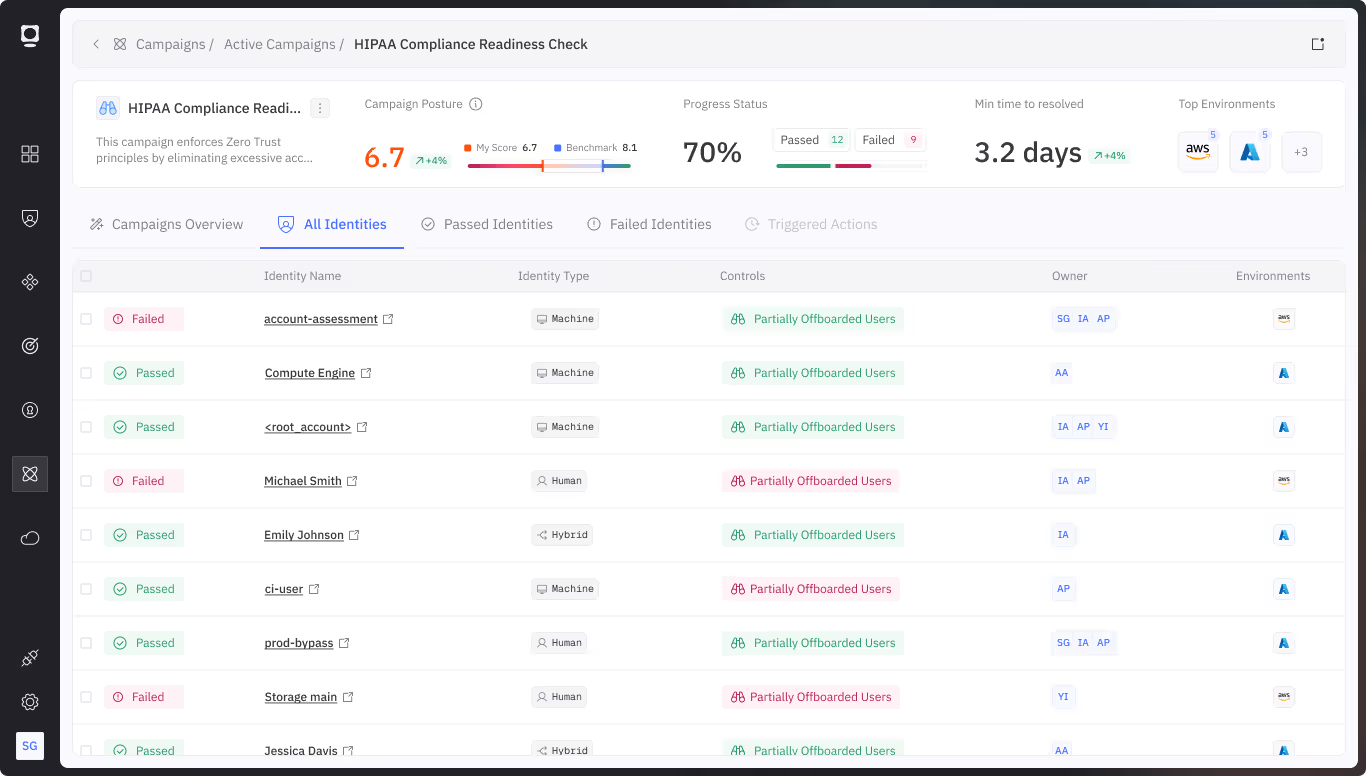
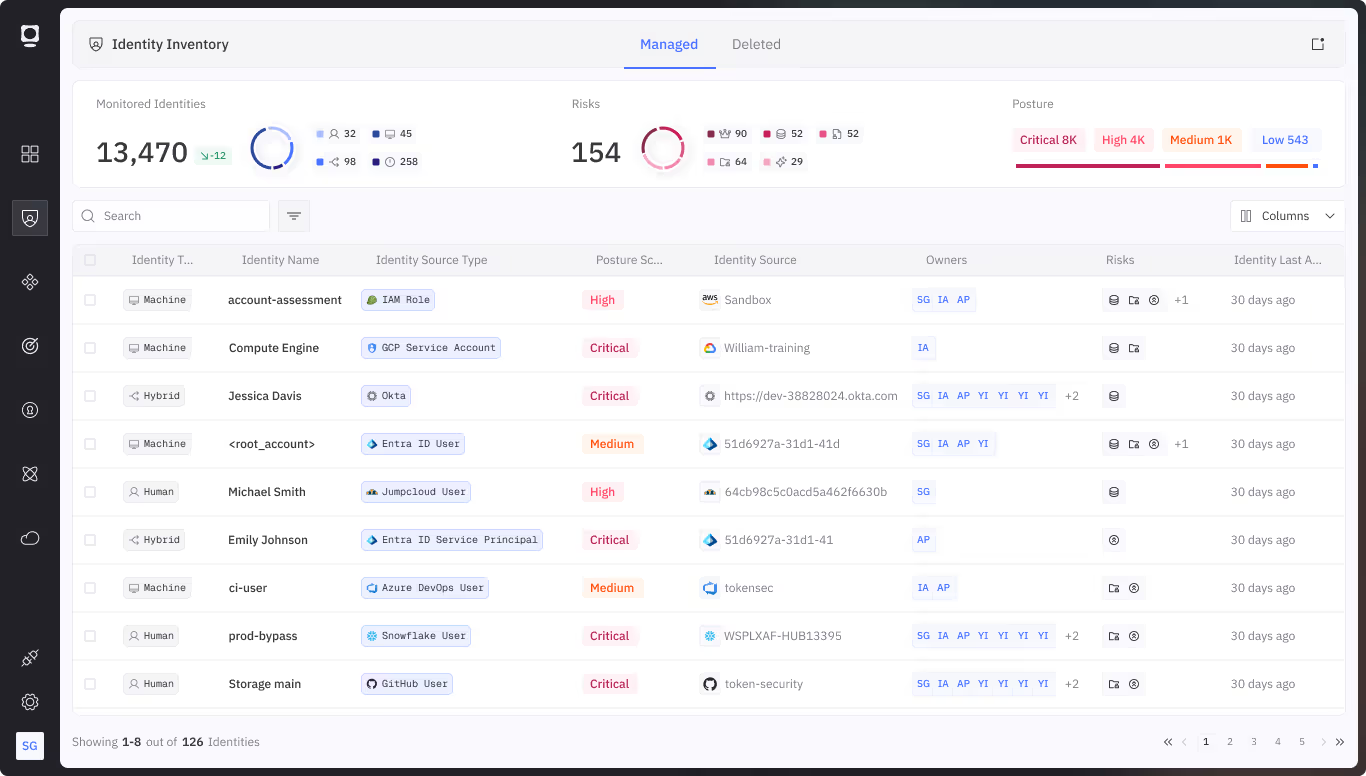
Machine identities used by third parties often operate outside your standard security processes. This is true whether they belong to contractors, SaaS integrations, or supply chain partners. These NHIs can have persistent access to sensitive systems, but lack the governance and monitoring of internal identities.
Token Security automatically discovers NHIs, classifies them by organization and function, and maps their access across cloud, SaaS, on-prem, and AI environments. With continuous posture assessment, secrets management, and alerting on behavioral anomalies, you can extend security controls beyond your perimeter without adding friction to partner workflows.
Features
The Solution
Machine identities used by third parties often operate outside your standard security processes. This is true whether they belong to contractors, SaaS integrations, or supply chain partners. These NHIs can have persistent access to sensitive systems, but lack the governance and monitoring of internal identities.
Token Security automatically discovers NHIs, classifies them by organization and function, and maps their access across cloud, SaaS, on-prem, and AI environments. With continuous posture assessment, secrets management, and alerting on behavioral anomalies, you can extend security controls beyond your perimeter without adding friction to partner workflows.
Capabilities

Discover machine identities used by third parties
Identify service accounts, bots, API clients, and AI agents accessed by vendors, partners, or external developers.

Track entitlements and access paths
Map out exactly what systems and data these NHIs can reach, and flag overly broad or persistent permissions.

Apply governance and access boundaries
Enforce limits on scope, duration, and privileges for third-party access based on policy or risk level.

Detect idle or orphaned third-party NHIs
Automatically flag unused external NHIs that may have been forgotten or abandoned.

Enable vendor-specific alerts and remediation
Route alerts to the appropriate internal teams based on vendor.
Discover Other Use Cases
The Agentic AI Security Challenge
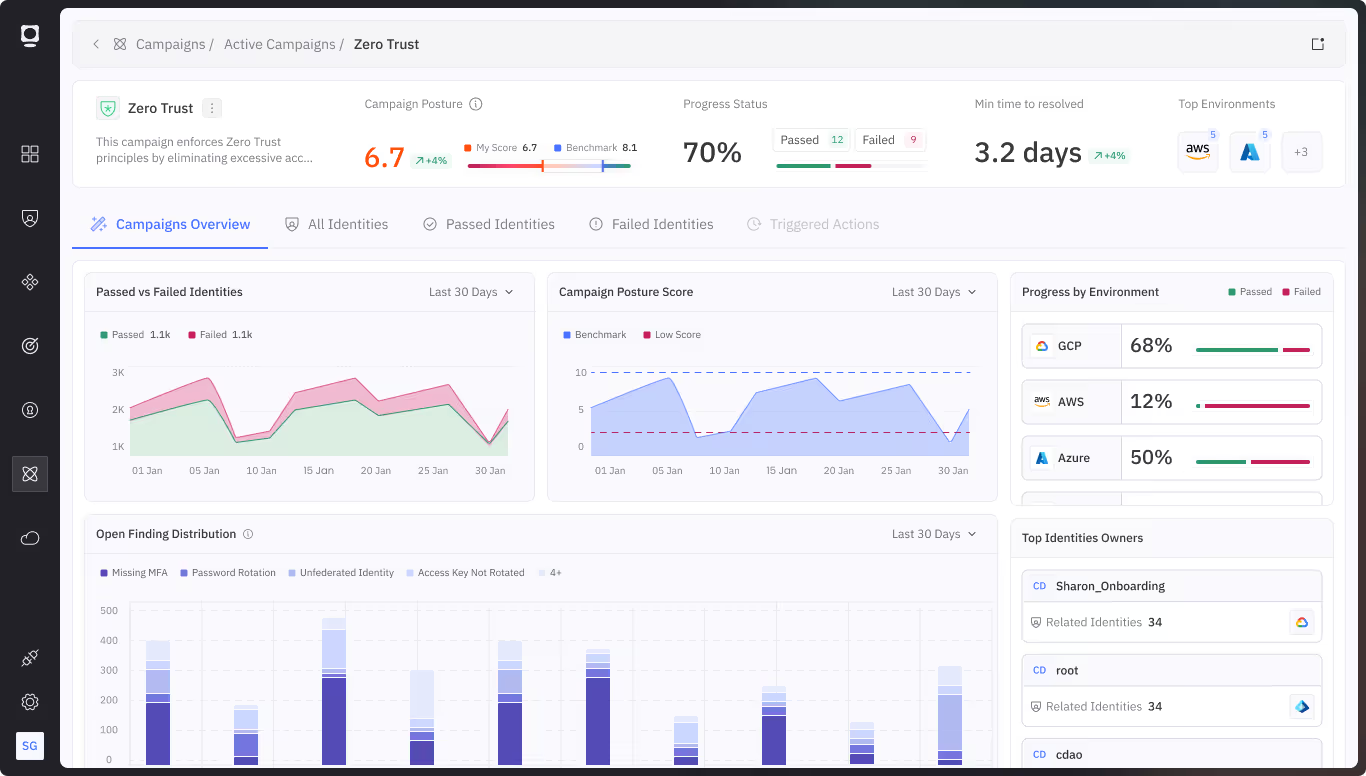
Organizations are racing to adopt agentic AI to enable innovation, gain a competitive advantage, and realize operational efficiencies. But with rapid adoption comes real risk, and today’s identity and access controls aren’t built for autonomous agents.
Identity Sprawl,
Out of Control
AI agents multiply unchecked, creating unmanaged identities and orphaned accounts with lingering access
Unpredictable AI Behavior, Zero Accountability
Autonomous agents act unpredictably, making it nearly impossible to trace actions and detect anomalies
Over-Privileged Agents, Expanded Attack Surface
Excessive, long-lived permissions leave AI agents dangerously overexposed to compromise
One Breach, Organizational Compromise
A single compromised AI agent can cascade across systems, amplifying damage instantly
Static Secrets, Zero Trust Blind Spots
Unrotated API keys or stale tokens without MFA protection, create exploitable security gaps
Securing Agentic AI at Scale
The Token Security Solution
The Token Security platform is purpose-built to secure the identities supporting agentic AI deployments by delivering visibility, control, and governance that enterprises need to secure AI at scale. Key capabilities include:

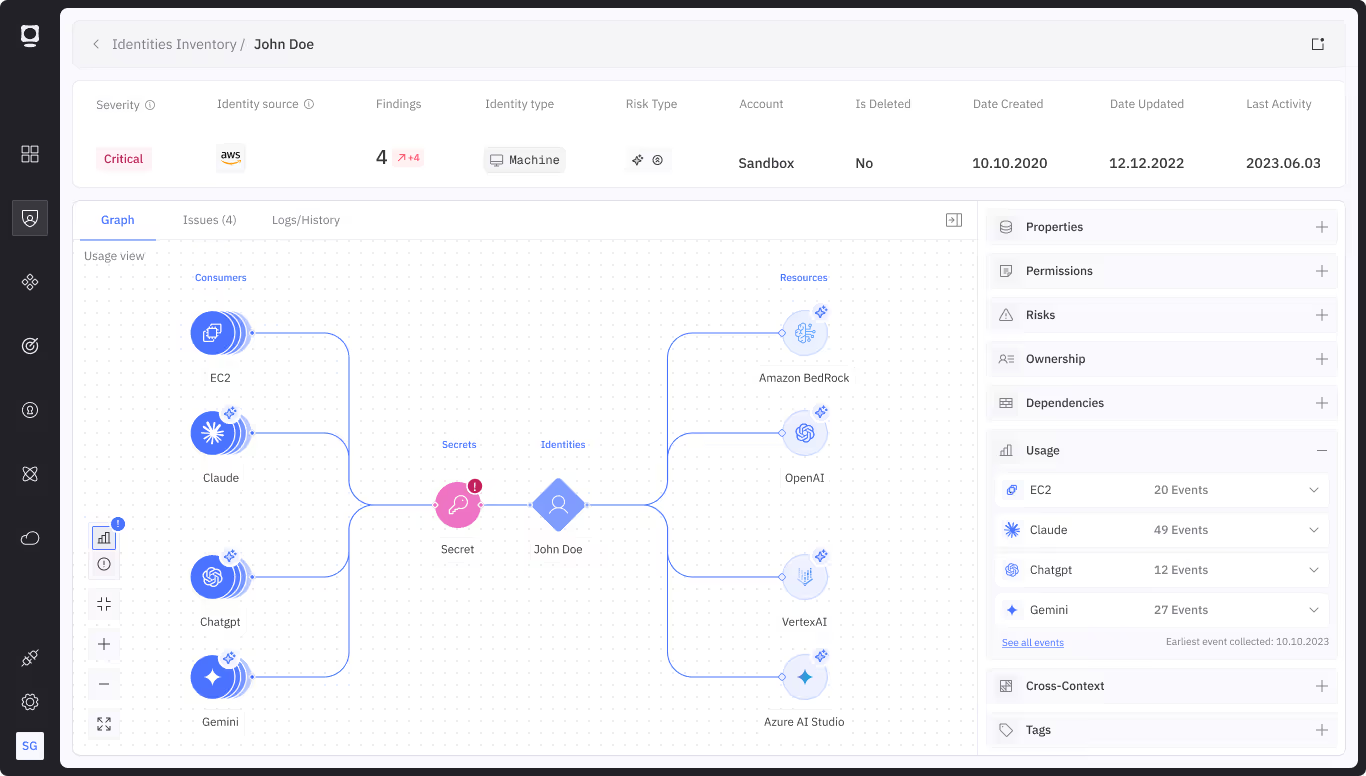
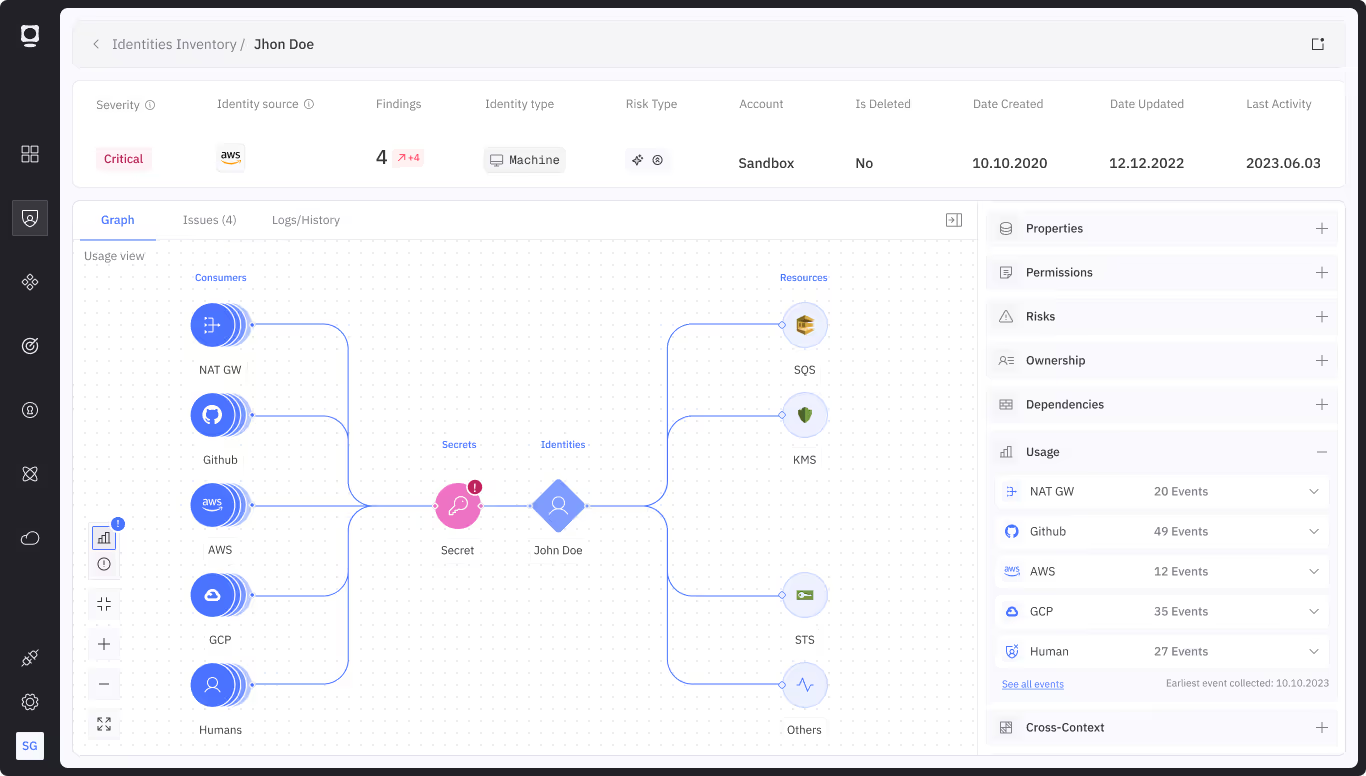
Discover Hidden AI Agents and MCP Servers
Automatically uncover Shadow AI and MCP servers, giving you complete visibility and eliminating blind spots

Establish AI Agent Ownership and Accountability
Assign ownership, rotate credentials, and retire orphaned agents before they become long-term risks

Enforce AI Agent Access Control and Right-Sizing
Continuously enforce least privilege and just-in-time access, remediating excessive permissions in real time

Ensure Traceability in a Multi-Agent Ecosystem
Log every AI agent action across ecosystems, ensuring compliance and rapid incident investigation
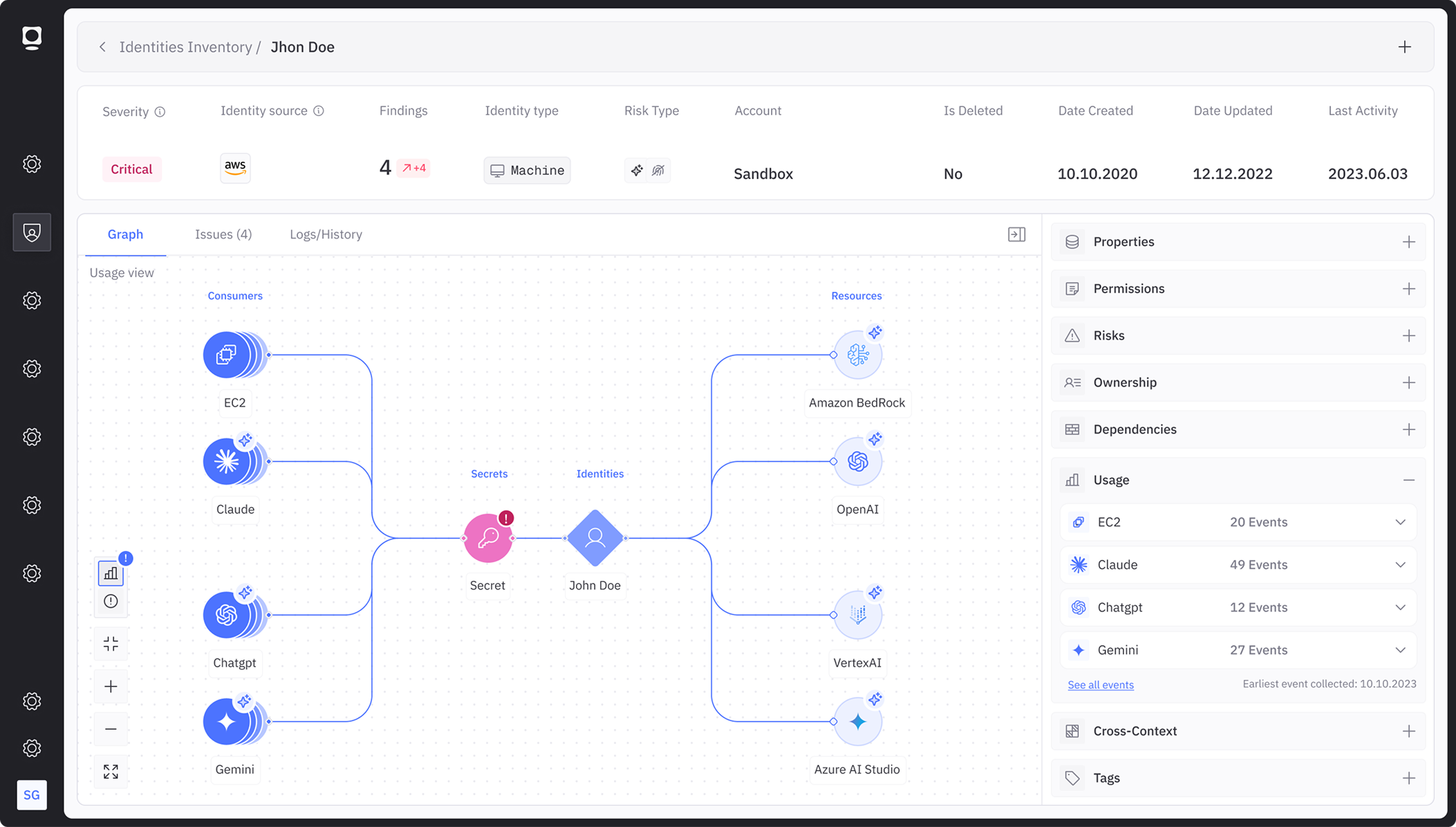
Plug Token Security Into Your AI Stack
Integrate with your existing AI frameworks to get instant visibility and control over every agent. Token Security connects to your managed AI ecosystems, so you don’t just discover shadow AI, you inventory the agents you already run, establish ownership, map their access, and right-size permissions.
Works with your AI frameworks
What Sets Token Security Apart
Token Security is built for organizations that need more than discovery. From AI agent identity hygiene to intelligent remediation, we deliver uncompromising control, so you can trust your AI infrastructure.
Contextual Awareness:
End-to-end AI Agent Lifecycle Control:
Intelligent Remediation at Scale:
Integrated Privilege Governance:
Real-Time Threat Response:
Ready to See Token Security in Action?
Token Security empowers CISOs and security and identity teams to embrace agentic AI safely and securely without compromising innovation, agility, and compliance.
Request a DemoThe Challenge
Business Impact

Discover machine identities used by third parties
Identify service accounts, bots, API clients, and AI agents accessed by vendors, partners, or external developers.

Track entitlements and access paths
Map out exactly what systems and data these NHIs can reach, and flag overly broad or persistent permissions.

Apply governance and access boundaries
Enforce limits on scope, duration, and privileges for third-party access based on policy or risk level.
The Token Security Solution

.gif)