Mergers & Acquisitions
Quickly assess and secure non-human identities across merging environments to reduce risk and streamline consolidation.



The Solution
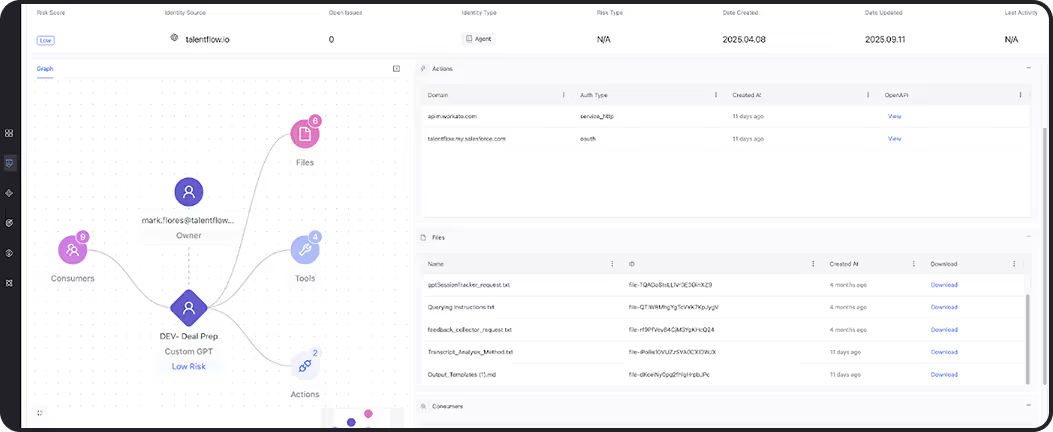
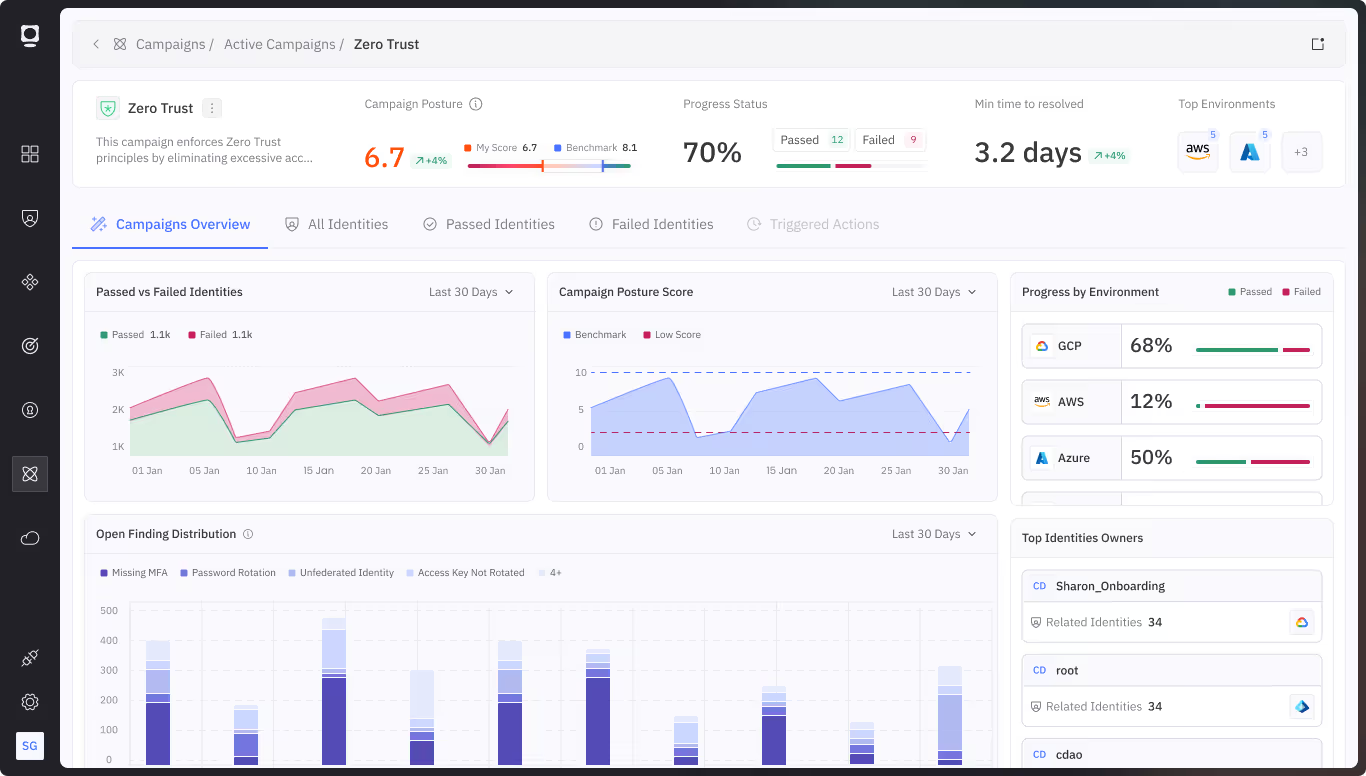
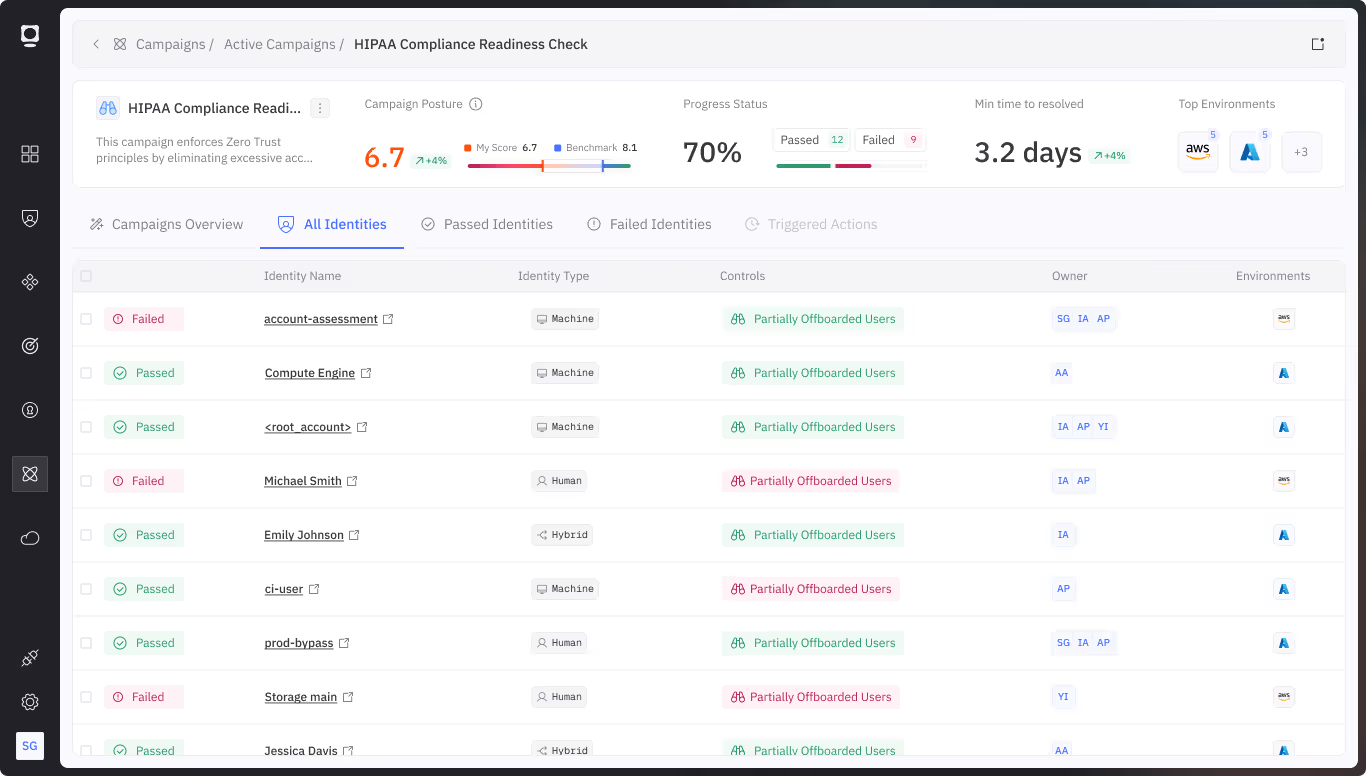
Merger and acquisition (M&A) activities introduce complex identity challenges: redundant systems, inherited technical debt, unmanaged credentials, and conflicting policies. Non-human identities are especially vulnerable—often overlooked during integration and difficult to trace across environments.
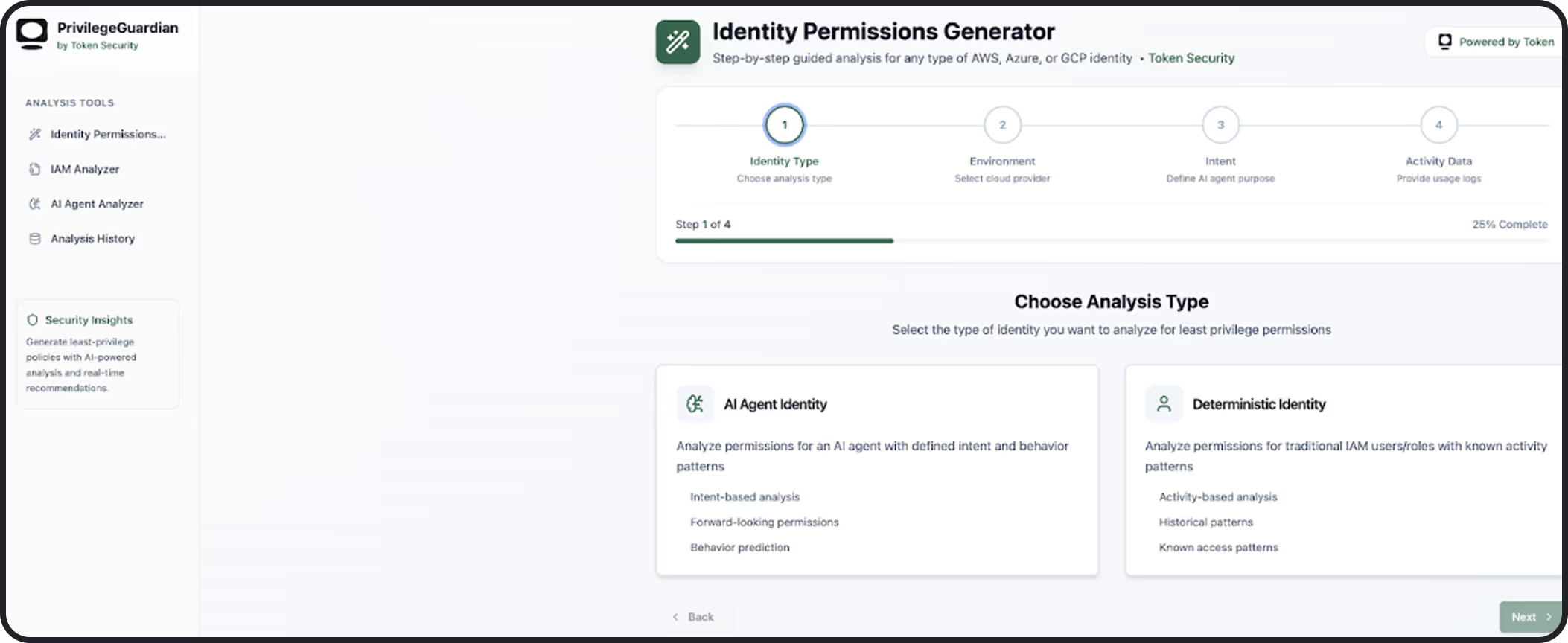
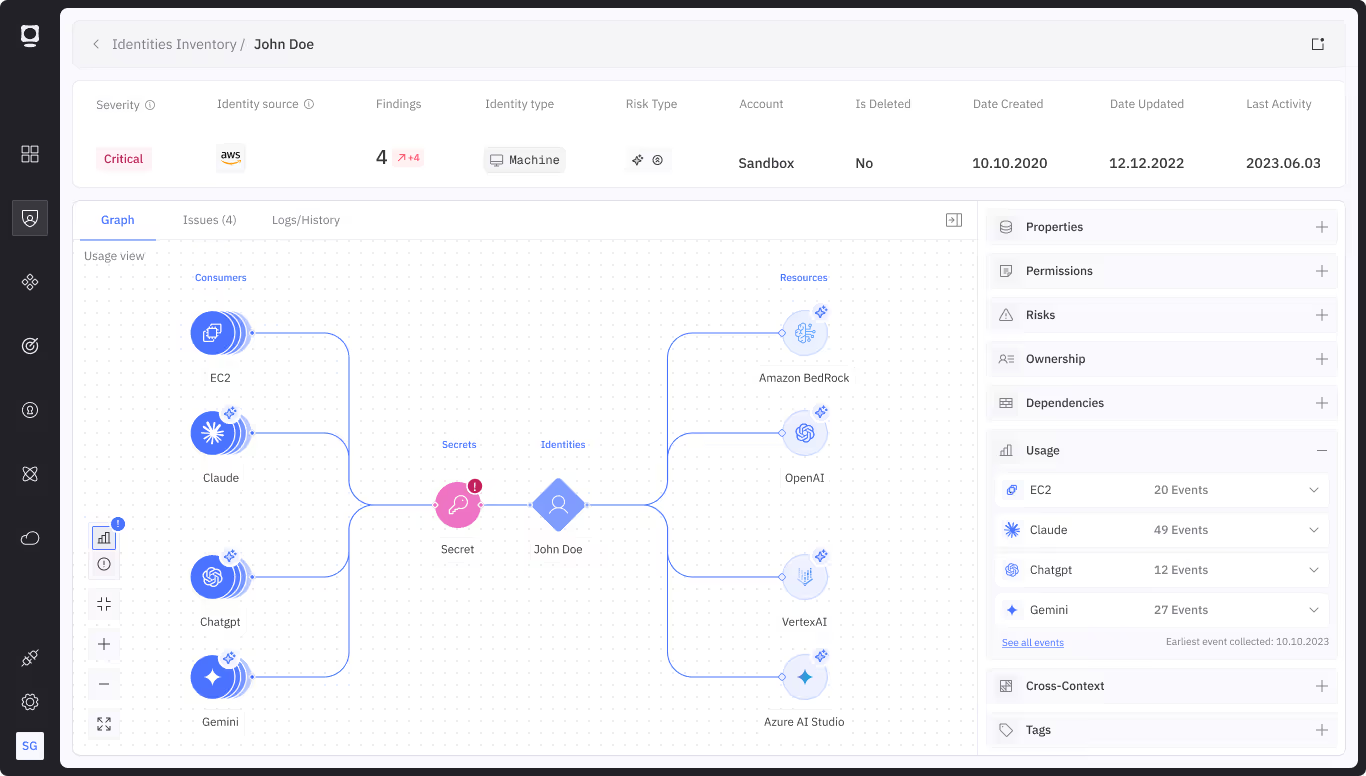
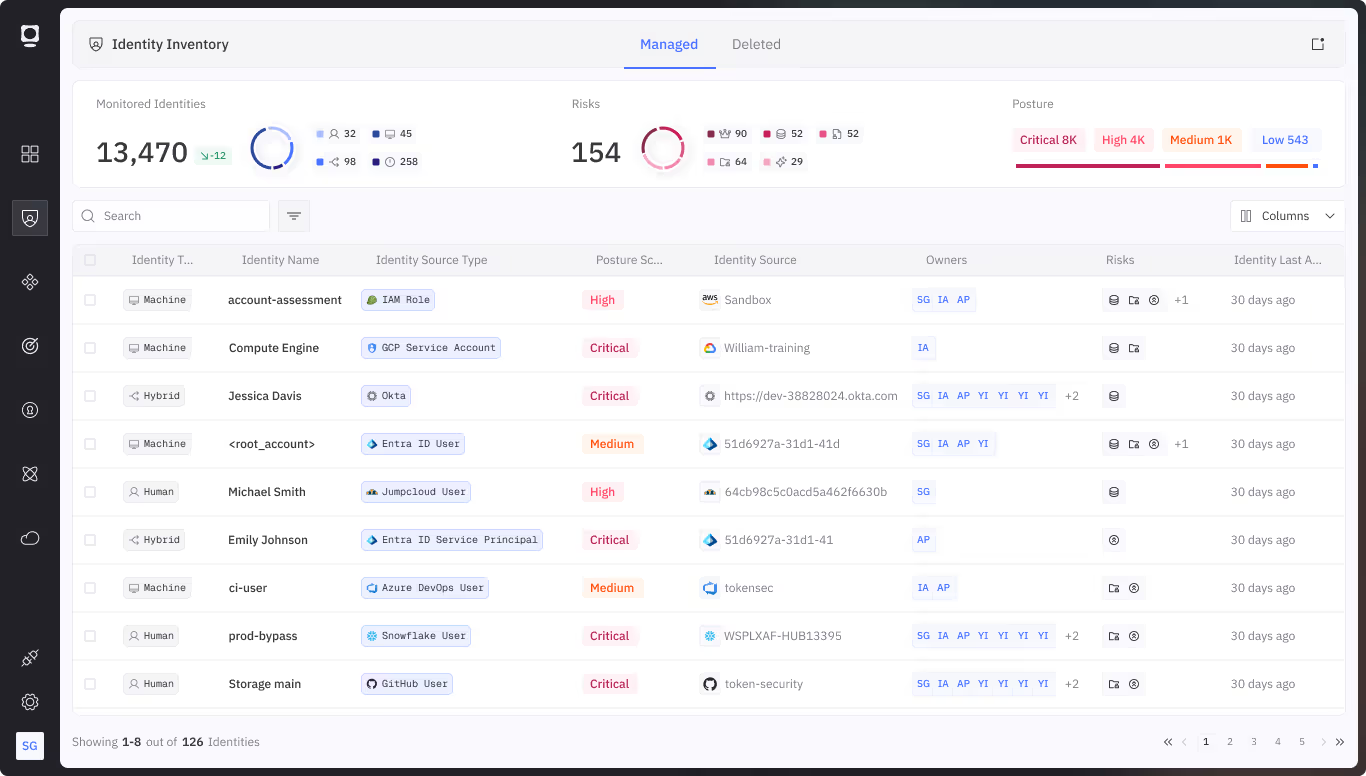
Token Security provides rapid visibility into all machine identities from both acquiring and acquired entities. It classifies and maps access paths, detects unmanaged or high-risk accounts, and highlights policy gaps. With automation to remediate stale credentials, enforce consistent governance, and align access with risk, Token Security helps teams accelerate secure integration without adding operational drag.
Features
The Solution
Merger and acquisition (M&A) activities introduce complex identity challenges: redundant systems, inherited technical debt, unmanaged credentials, and conflicting policies. Non-human identities are especially vulnerable—often overlooked during integration and difficult to trace across environments.
Token Security provides rapid visibility into all machine identities from both acquiring and acquired entities. It classifies and maps access paths, detects unmanaged or high-risk accounts, and highlights policy gaps. With automation to remediate stale credentials, enforce consistent governance, and align access with risk, Token Security helps teams accelerate secure integration without adding operational drag.
Capabilities

Rapidly discover NHIs across merged environments
Automatically build a unified inventory of machine identities across clouds, data centers, and platforms.

Detect duplicate or conflicting identities
Identify overlapping service accounts or identities with inconsistent permissions and roles across organizations.

Prioritize risk across inherited systems
Score NHIs by risk, blast radius, and compliance exposure to focus on what matters most during integration.

Normalize and enforce consistent access policies
Bring legacy or external environments into alignment with current governance practices.

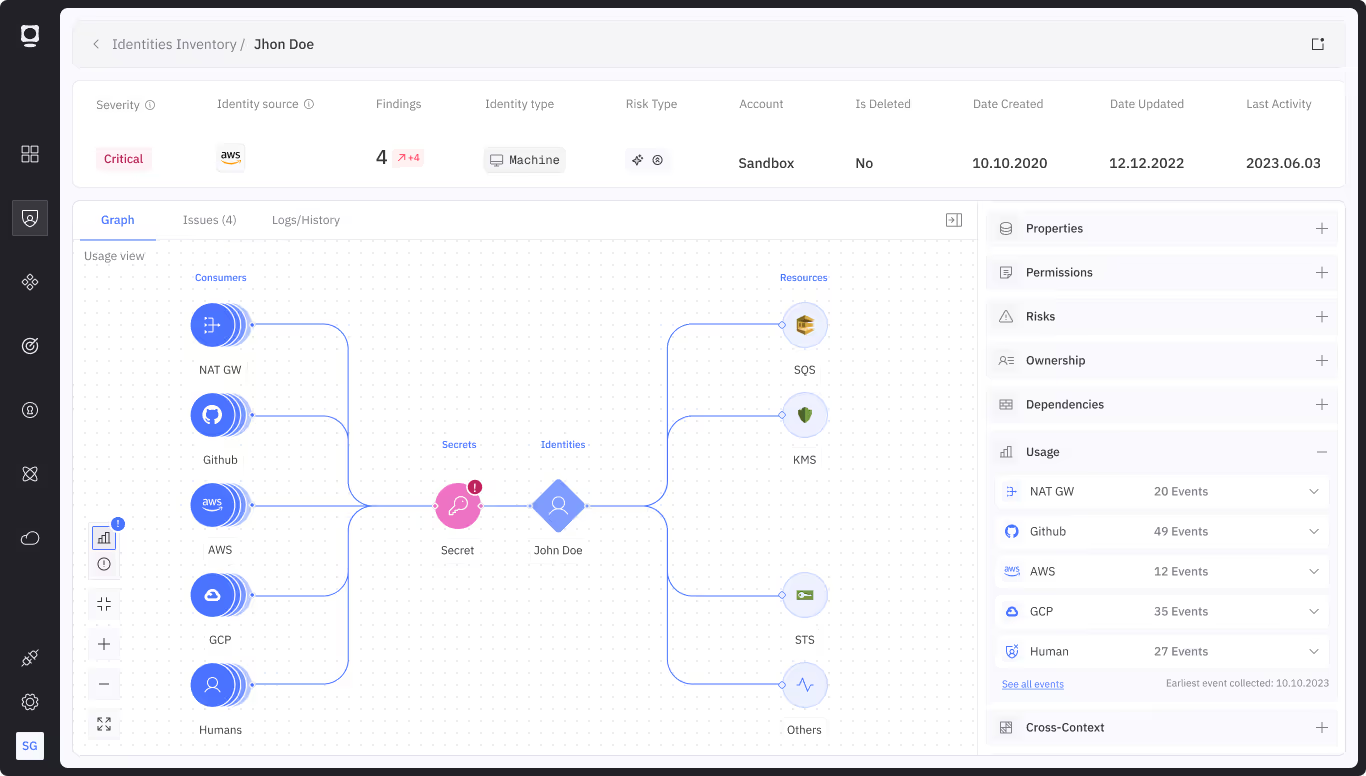
Accelerate credential cleanup and rationalization
Automatically flag and decommission unused secrets, tokens, or keys that could linger from the previous entity.
Discover Other Use Cases
The Agentic AI Security Challenge
Organizations are racing to adopt agentic AI to enable innovation, gain a competitive advantage, and realize operational efficiencies. But with rapid adoption comes real risk, and today’s identity and access controls aren’t built for autonomous agents.
Identity Sprawl,
Out of Control
AI agents multiply unchecked, creating unmanaged identities and orphaned accounts with lingering access
Unpredictable AI Behavior, Zero Accountability
Autonomous agents act unpredictably, making it nearly impossible to trace actions and detect anomalies
Over-Privileged Agents, Expanded Attack Surface
Excessive, long-lived permissions leave AI agents dangerously overexposed to compromise
One Breach, Organizational Compromise
A single compromised AI agent can cascade across systems, amplifying damage instantly
Static Secrets, Zero Trust Blind Spots
Unrotated API keys or stale tokens without MFA protection, create exploitable security gaps
Securing Agentic AI at Scale
The Token Security Solution
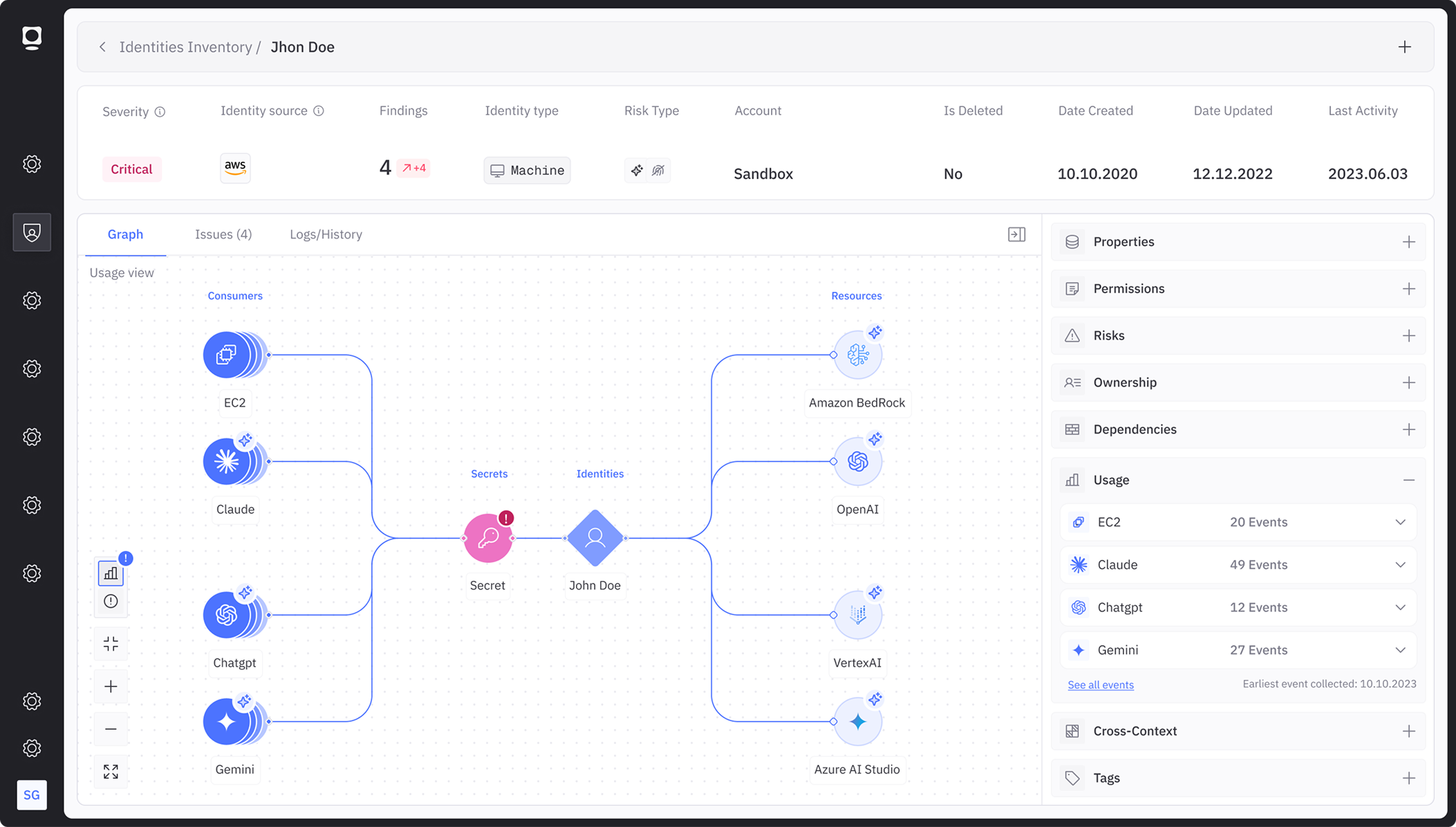
The Token Security platform is purpose-built to secure the identities supporting agentic AI deployments by delivering visibility, control, and governance that enterprises need to secure AI at scale. Key capabilities include:

Discover Hidden AI Agents and MCP Servers
Automatically uncover Shadow AI and MCP servers, giving you complete visibility and eliminating blind spots

Establish AI Agent Ownership and Accountability
Assign ownership, rotate credentials, and retire orphaned agents before they become long-term risks

Enforce AI Agent Access Control and Right-Sizing
Continuously enforce least privilege and just-in-time access, remediating excessive permissions in real time

Ensure Traceability in a Multi-Agent Ecosystem
Log every AI agent action across ecosystems, ensuring compliance and rapid incident investigation
Plug Token Security Into Your AI Stack
Integrate with your existing AI frameworks to get instant visibility and control over every agent. Token Security connects to your managed AI ecosystems, so you don’t just discover shadow AI, you inventory the agents you already run, establish ownership, map their access, and right-size permissions.
Works with your AI frameworks
What Sets Token Security Apart
Token Security is built for organizations that need more than discovery. From AI agent identity hygiene to intelligent remediation, we deliver uncompromising control, so you can trust your AI infrastructure.
Contextual Awareness:
End-to-end AI Agent Lifecycle Control:
Intelligent Remediation at Scale:
Integrated Privilege Governance:
Real-Time Threat Response:
Ready to See Token Security in Action?
Token Security empowers CISOs and security and identity teams to embrace agentic AI safely and securely without compromising innovation, agility, and compliance.
Request a DemoThe Challenge
Business Impact

Rapidly discover NHIs across merged environments
Automatically build a unified inventory of machine identities across clouds, data centers, and platforms.

Detect duplicate or conflicting identities
Identify overlapping service accounts or identities with inconsistent permissions and roles across organizations.

Prioritize risk across inherited systems
Score NHIs by risk, blast radius, and compliance exposure to focus on what matters most during integration.
The Token Security Solution

.gif)