CVE-2026-21858: When Your Workflow Automation Becomes an Attack Vector
A critical vulnerability in n8n exposes the hidden identity sprawl in your automation tools
Workflow automation platforms like n8n have become essential to modern enterprises. They connect your CRM to Slack, sync data between cloud services, and automate countless business processes. But this convenience comes with a hidden cost: these tools accumulate credentials and identities across your entire infrastructure, often without security teams even knowing.
A newly disclosed critical 10.0 vulnerability in n8n (CVE-2026-21858) makes this risk painfully clear.
What Happened
Security researcher Dor Attias from Cyera discovered an unauthenticated remote code execution vulnerability in n8n. In plain terms, an attacker can take over your entire n8n environment without needing a password, gaining full access to everything, including all stored credentials and connected systems.
The fix is available in version 1.121.0 and later.
Why This Matters More Than a Typical RCE
The real danger isn't just the vulnerability itself, but what n8n has access to.
When we analyzed customer environments, we found that a single n8n deployment typically connects to dozens of services: AWS accounts, GCP projects, databases, SaaS applications, and internal APIs. Each connection requires credentials, and n8n stores those credentials so the instance can use them.
In our research across multiple enterprise environments, we identified hundreds of distinct identities tied to n8n deployments across many customers. This included connections to major cloud platforms like AWS and GCP, database credentials, OAuth integrations, API keys, access tokens, and more.
Here's what should concern every security leader: many of these weren't limited credentials with narrow permissions. We found API keys and access tokens with elevated privileges in production environments, some with full administrative access that would give an attacker complete control over critical systems and sensitive data.
How to Know If You're Exposed
Start by answering these questions:
Do you have n8n in your environment? This sounds obvious, but workflow tools often get deployed by teams outside of IT by marketing, operations, or individual developers. Check for n8n instances in your cloud environments, Kubernetes clusters, and container registries.
What version is running? If it's below 1.121.0, you're vulnerable. Prioritize internet-facing instances, but don't ignore internal deployments. Lateral movement is a real threat.
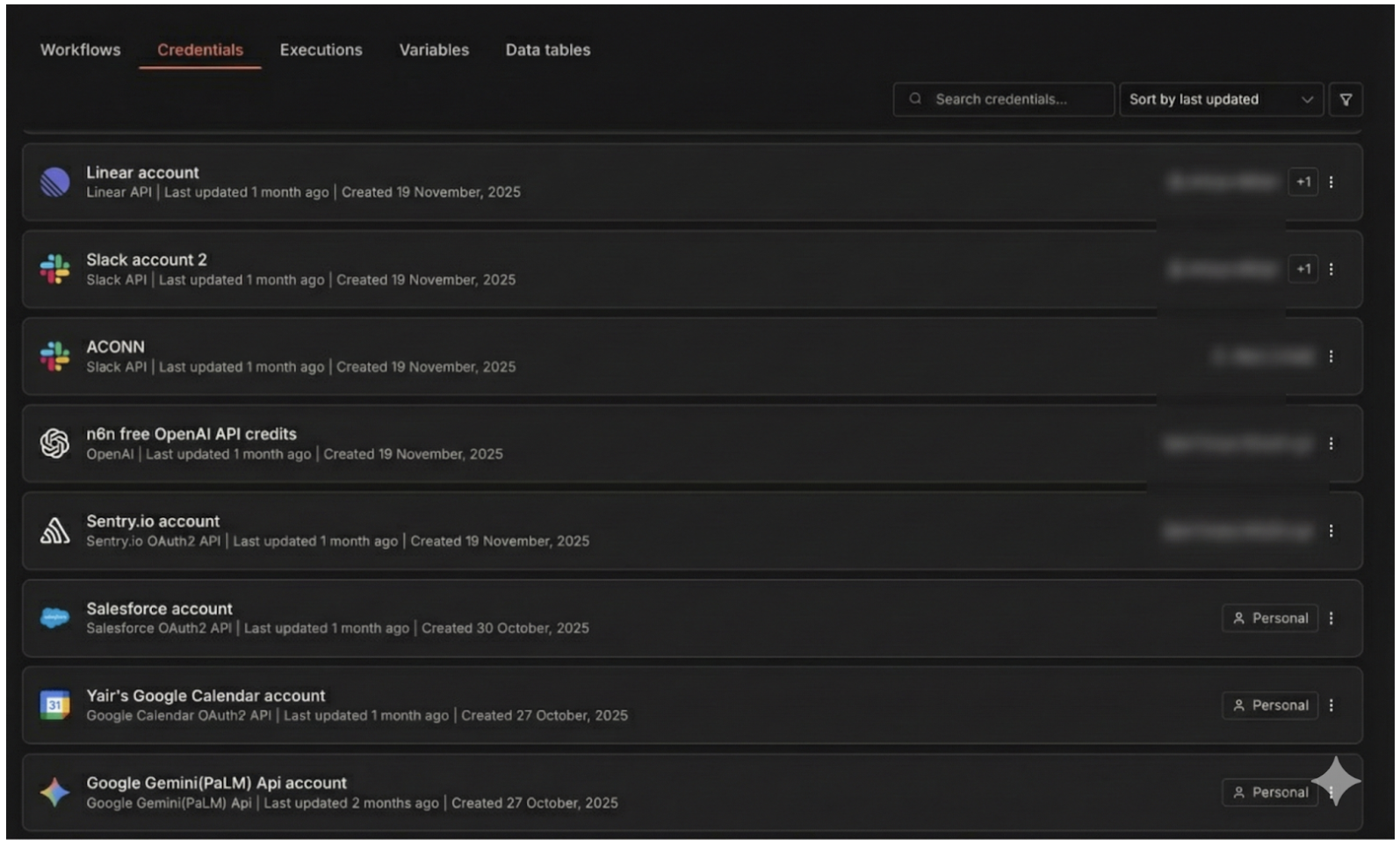
What can n8n access? This is the harder question. Review the workflows configured in your n8n instances. You can also navigate to the Credentials tab in n8n to see all stored credentials in one place. Each credential represents a potential exposure point.
Immediate Response Steps
For organizations with confirmed n8n deployments, we recommend a phased remediation approach.
In the first 24-48 hours, focus on upgrading n8n to version 1.121.0 or later. Rotate any secrets that were accessible to the n8n instance, especially database passwords and API keys that show recent access.
Over the following week, monitor for suspicious activity and conduct a thorough investigation of past actions. Pro tip: search your logs for requests made with n8n's User Agent to trace all activity originating from your n8n instances.
For the longer term, implement automated secret rotation for credentials. Establish a process for discovering and inventorying workflow automation deployments across your organization.
The Bigger Picture: Automation Tool Sprawl
This vulnerability highlights a broader challenge. Workflow automation tools are proliferating across enterprises, each one accumulating credentials and creating identity sprawl that traditional security tools don't track.
At Token Security, we help organizations rapidly identify and respond to vulnerabilities like this. Our platform automatically discovers non-human and AI agent identities across your environment, including workflow automation tools like n8n and the credentials they use.
When a new CVE drops, you can immediately see which identities are affected and what credentials are at risk. But the real value starts before the vulnerability is even discovered. Token Security continuously analyzes the permissions of every machine and AI agent identities in your environment, so you understand the potential blast radius in advance. By identifying overly permissive credentials and unnecessary access, you can reduce the impact of a future breach before it happens.
In the case of CVE-2026-21858, we enable our customers to identify all affected n8n identities within minutes, map out every credential at risk, and help them prioritize remediation based on actual permission levels, not guesswork.
See the Token Security platform in action. Request a demo today.
.gif)






