NHI Security Posture Management
Reduce your attack surface by mitigating identity-based risks while aligning with security and regulatory requirements.




The Solution
A strong NHI security posture means continuously monitoring risks, tracking threats, closing security gaps, and ensuring security policies are enforced and audit-ready to meet internal and regulatory compliance mandates. Token Security continuously scores NHI risks by context, access, usage, and potential blast radius—prioritizing what matters most for both security and compliance.
Features

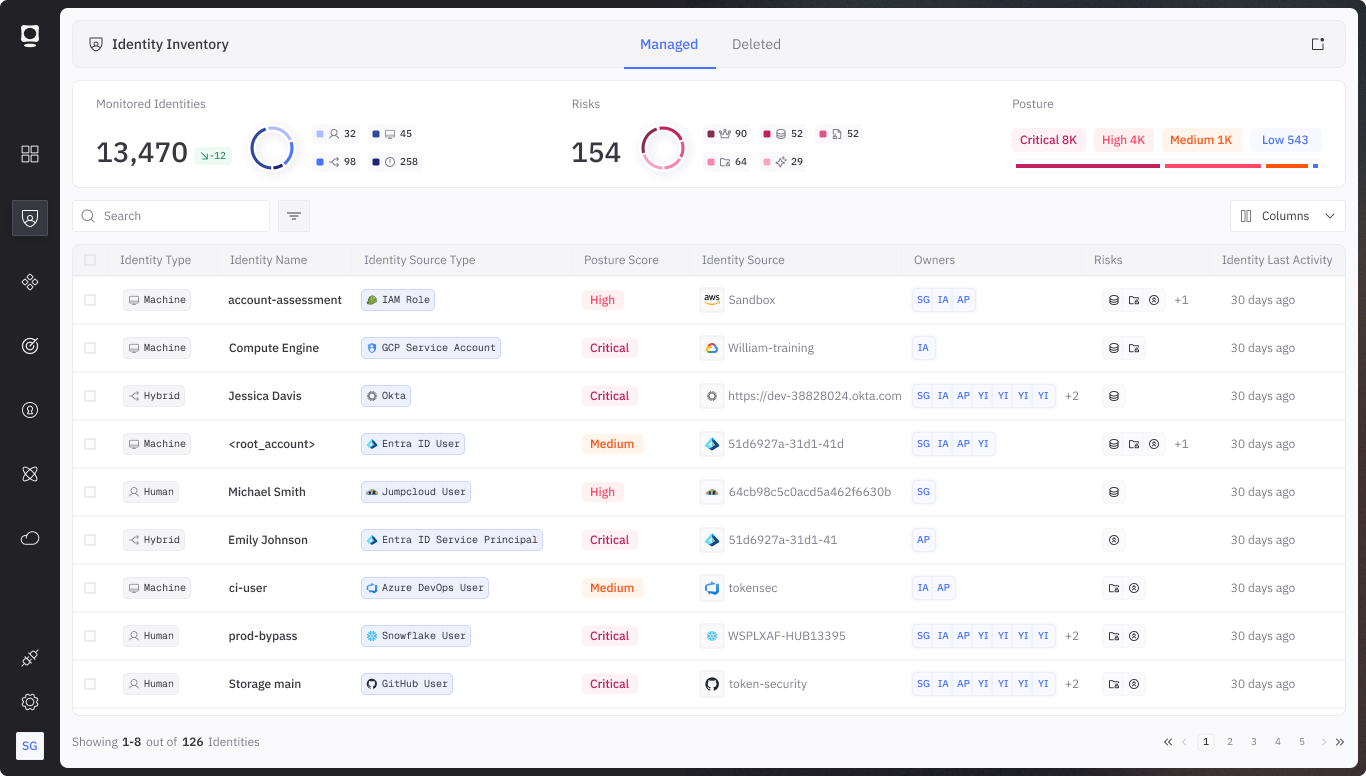
Manage risk according to benchmarks
Get an overview of NHI security posture compared to an industry benchmark, highlighting total identities across all environments, risk levels, key rotation overview across all auth types, top risky identities, and critical security insights across all environments, from on-prem to cloud.

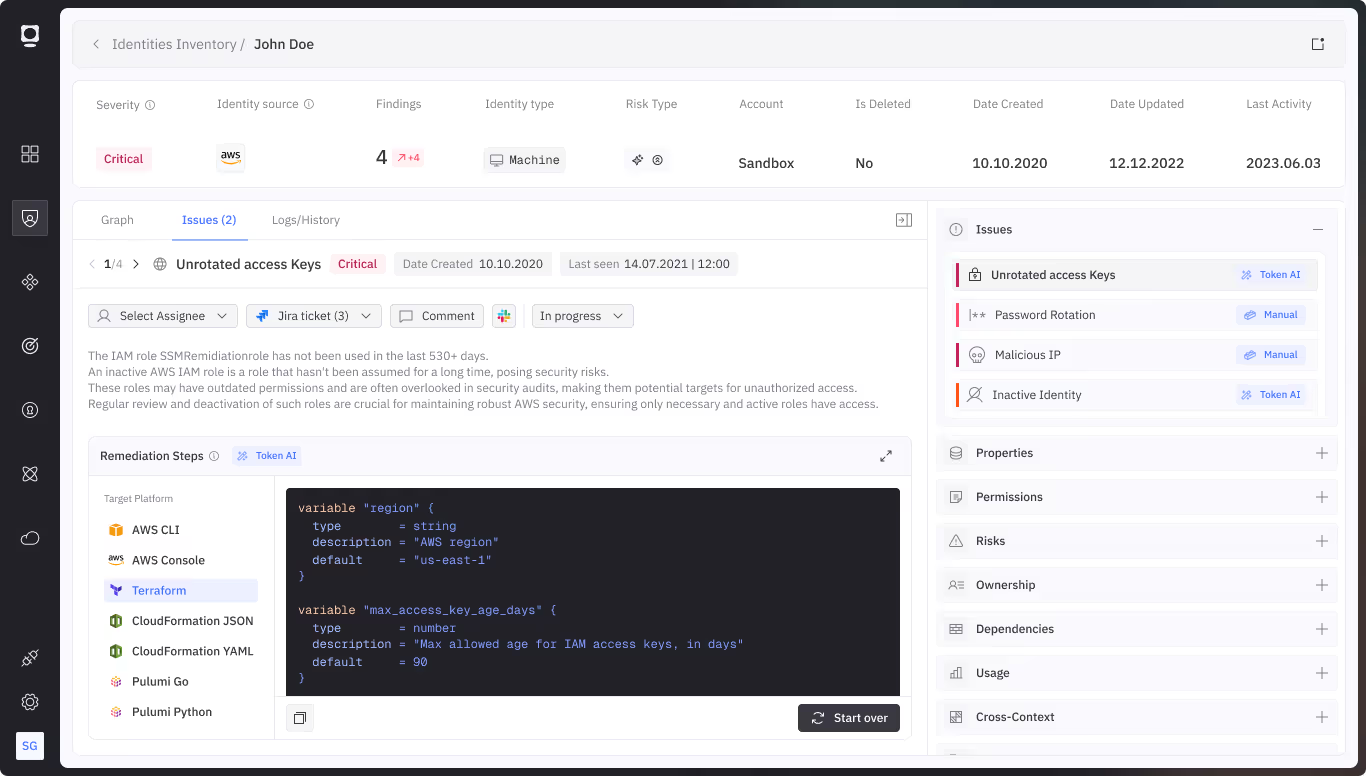
Mitigate risks based on criticality and potential blast radius
Have the ability to prioritize risks based on potential impact, permissions, and other metrics for immediate attention.

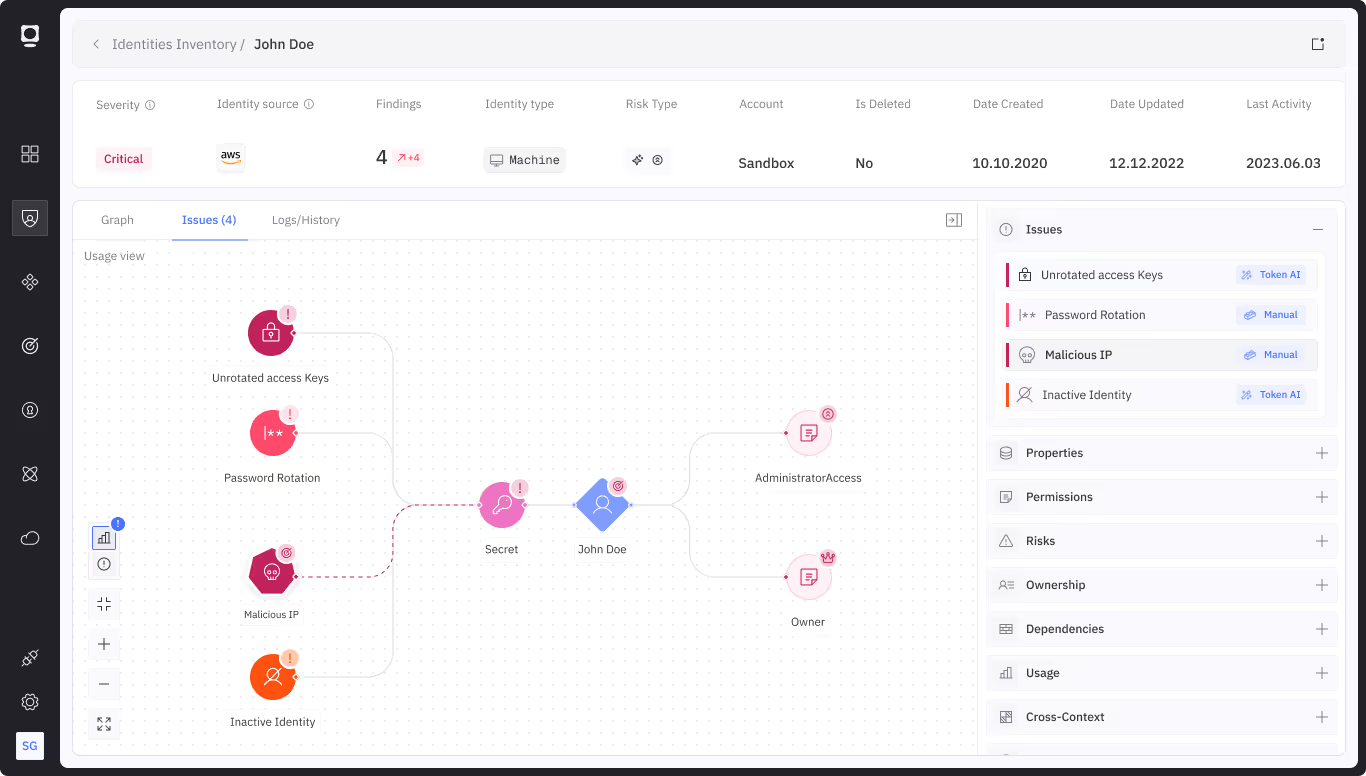
Identify orphaned identities
Find unused, orphaned, or dormant NHIs that create an unnecessary attack surface.

Detect risky secrets
Find exposed and mismanaged secrets. Flag identities with redundant or excessive keys and and tokens to reduce sprawl and potential abuse. Identify forgotten access keys that are no longer used.

Identify overly permissive access
Analyze permissions and usage to identify permissive access given to NHIs. Identify unintended cross-account access, from Dev/Staging to Production.
Discover Other Capablities
The Token Security MCP Server and AI Agent combine to provide you with AI‑powered data analysis and guidance where you need it. Whether you prefer to work directly in our platform or connect to your own MCP servers and workflows, Token Security has you covered. Security, Identity and Access Management, and Development teams can now ask questions and make requests such as:
The Token MCP Server
Designed to be consumed from your tool of choice, the Token MCP Server enables you to ask questions from your favorite chat application (e.g., Claude, ChatGPT, Gemini) or AI Agent-based application (e.g., Cursor).
The Token AI Agent
Built directly into the Token Security NHI Security Platform, the Token AI agent gives you native conversational AI capabilities right from the Token UI.
Drive business outcomes with AI
The Token Security platform delivers AI-powered experiences, enabling intelligent querying, remediation, and posture insights through natural language to protect non-human identities at scale.
Token Security AI enables security teams to ask complex questions about their non-human identity inventory using natural language. Teams can explore Token findings, request intelligent recommendations, and receive clear, actionable guidance for resolving security posture issues - all through a seamless, conversational interface.
Token AI supports dynamic querying across all major data layers within the platform, including the NHI Inventory, NHI Security Posture Management, Lifecycle Management, Secrets, and Threat Detection and Response, giving users instant insights, explanations, and guided remediation recommendations.


Token AI benefits


Enhanced
Visibility
Token AI empowers users to ask complex, natural-language questions across their NHI inventory, permission structures, authentication methods, associated risks, environment criticality, ownership, and usage patterns. It automatically compiles and analyzes disparate data points to deliver a prioritized and actionable view of machine identity risks: something that is often difficult and time-consuming to achieve manually.

Smarter, Context-
Aware Remediation
Token AI delivers organization-specific remediation guidance, including scripts, CLI commands, and fix recommendations tailored to your environments. It helps security teams quickly understand what to fix, how to fix it, why it matters, and what the impact will be - saving hours of manual investigation and accelerating time-to-resolution for both security and cloud engineering teams.
See the Power of
Token AI in Action!
Token AI translates plain-language queries into Token platform-specific operations, such as querying the inventory, assessing risks, understanding the Identity blast radius, and generating qualified insights.
Token Security
AI Integration

Token AI doesn’t just bring AI to your security data - it connects directly into the broader Agentic AI ecosystem. By adhering to the open MCP standard, Token enables seamless integration with autonomous AI agents in tools like ChatGPT, Claude, and Cursor. This allows these agents to reason about NHI posture, retrieve findings, generate remediation scripts, and even initiate actions without requiring human input.
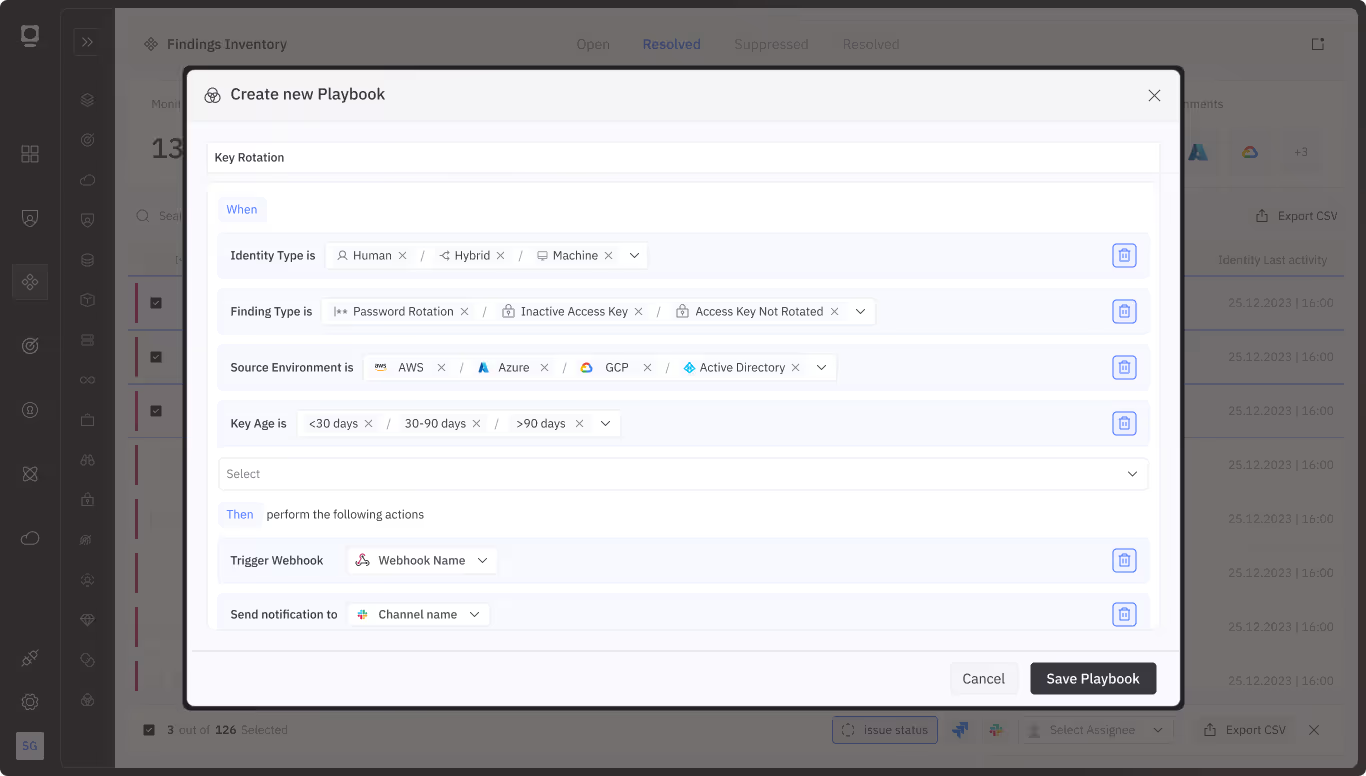
These integrations unlock powerful workflows where agents can autonomously identify risks, prioritize fixes, generate JIRA tickets with pre-filled scripts, notify stakeholders via Slack, and follow up on unresolved issues. The result is a shift from reactive security dashboards to proactive, intelligent assistants that operate continuously, driving faster resolution, improved compliance, and a stronger overall security posture.

.gif)