






Unseen. Unsecured.
Out of Control.
As AI use explodes, enterprises face a new class of identity threat: intelligent, autonomous agents with unchecked access to critical systems. These agents connect using identities that are:

Everywhere & Exploding
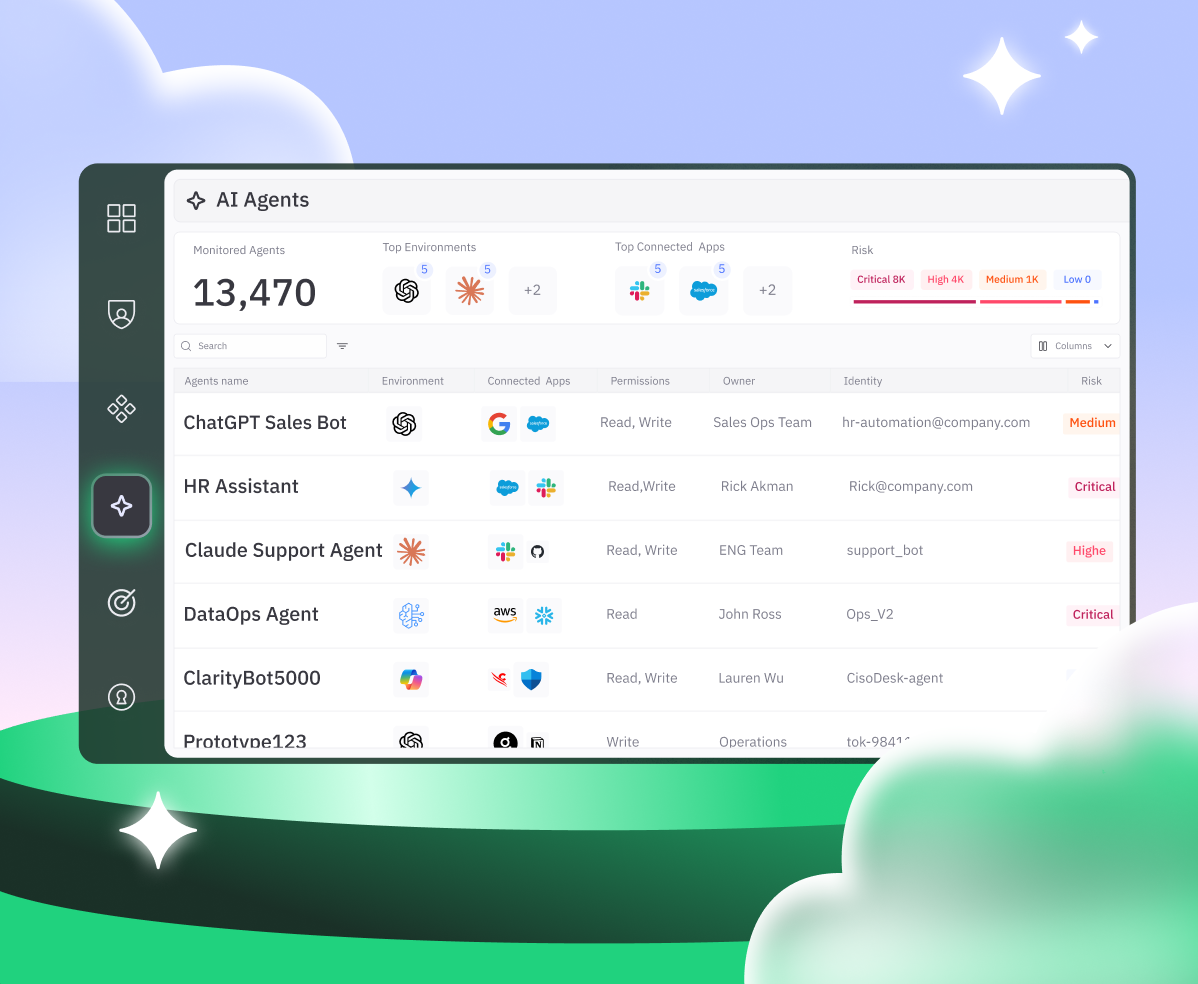
AI Agent and non-human identitites span across on-prem, cloud and AI platforms, while outnumbering human identities by 50:1.

Complex & Connected
A single compromised agent can trigger cascading damage across every connected system it touches.

Impossible to Remediate
Without understanding context and usage of each AI agent and identity, security and IAM teams fear breaking production systems.
Identity-First AI Agent Security
Token Security helps teams manage the full AI agent identity lifecycle, so they can adopt agentic AI quickly, without losing control.
AI-Native, Real-World Outcomes
We didn’t sprinkle AI on top. We built an integrated AI system, MCP + AI agents, to secure AI at scale.

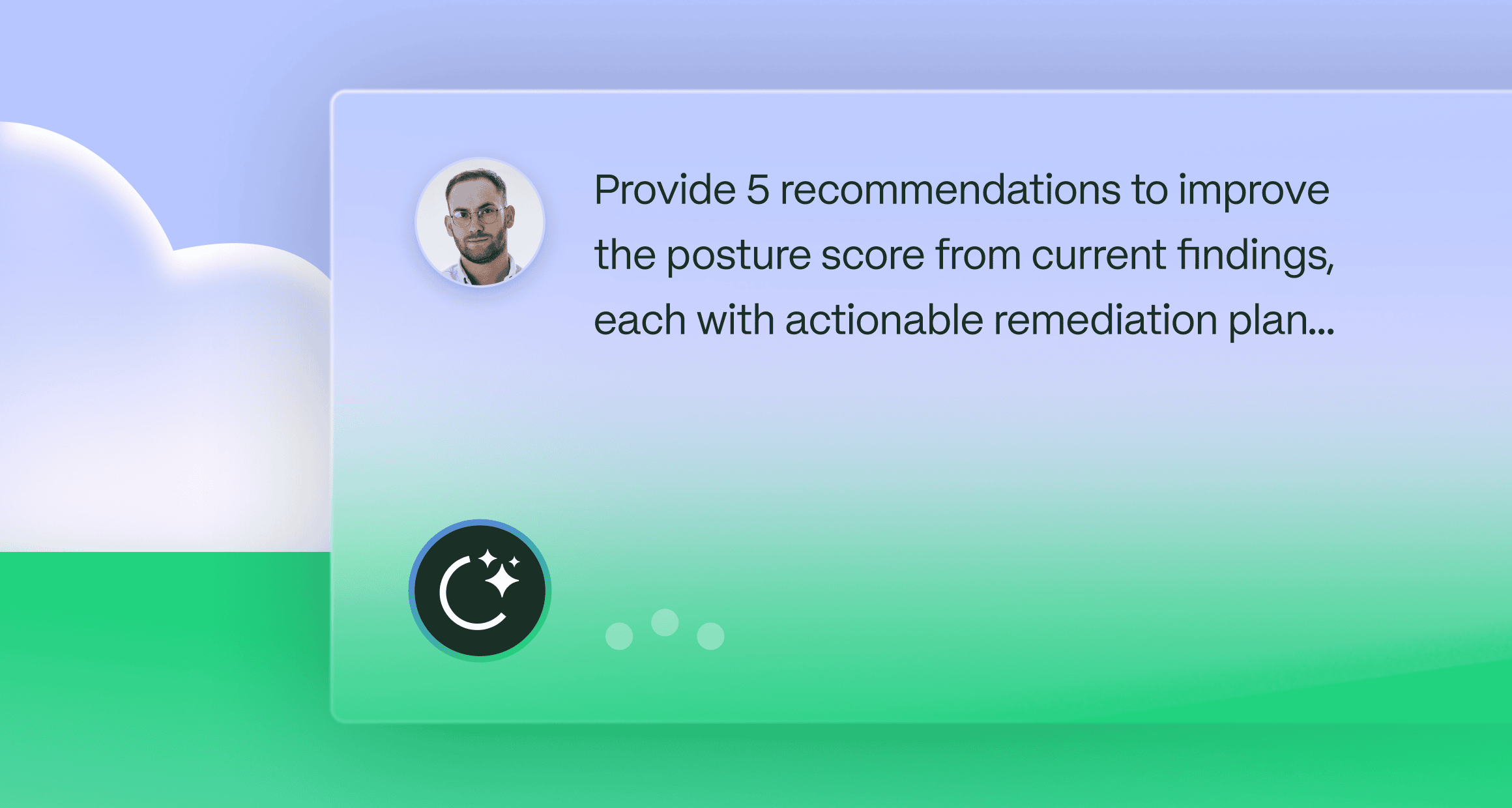
The Token MCP Server
Designed to be consumed from your tool of choice, the Token MCP Server enables you to ask questions from your favorite chat application (e.g., Claude, ChatGPT, Gemini) or AI Agent-based application (e.g., Cursor).


Token AI Agent
Built directly into the Token Security NHI Security Platform, the Token AI agent gives you native conversational AI capabilities right from the Token UI.
Why Token Security
Built for agentic AI
Token treats agents as first-class identities that require continuous discovery, governance, and control, moving beyond bolted-on policies on legacy, human-centric tools.
Identity is the Control Plane
Guardrails and prompt security fail when access is granted. Token secures agents at the identity level, where control is possible.
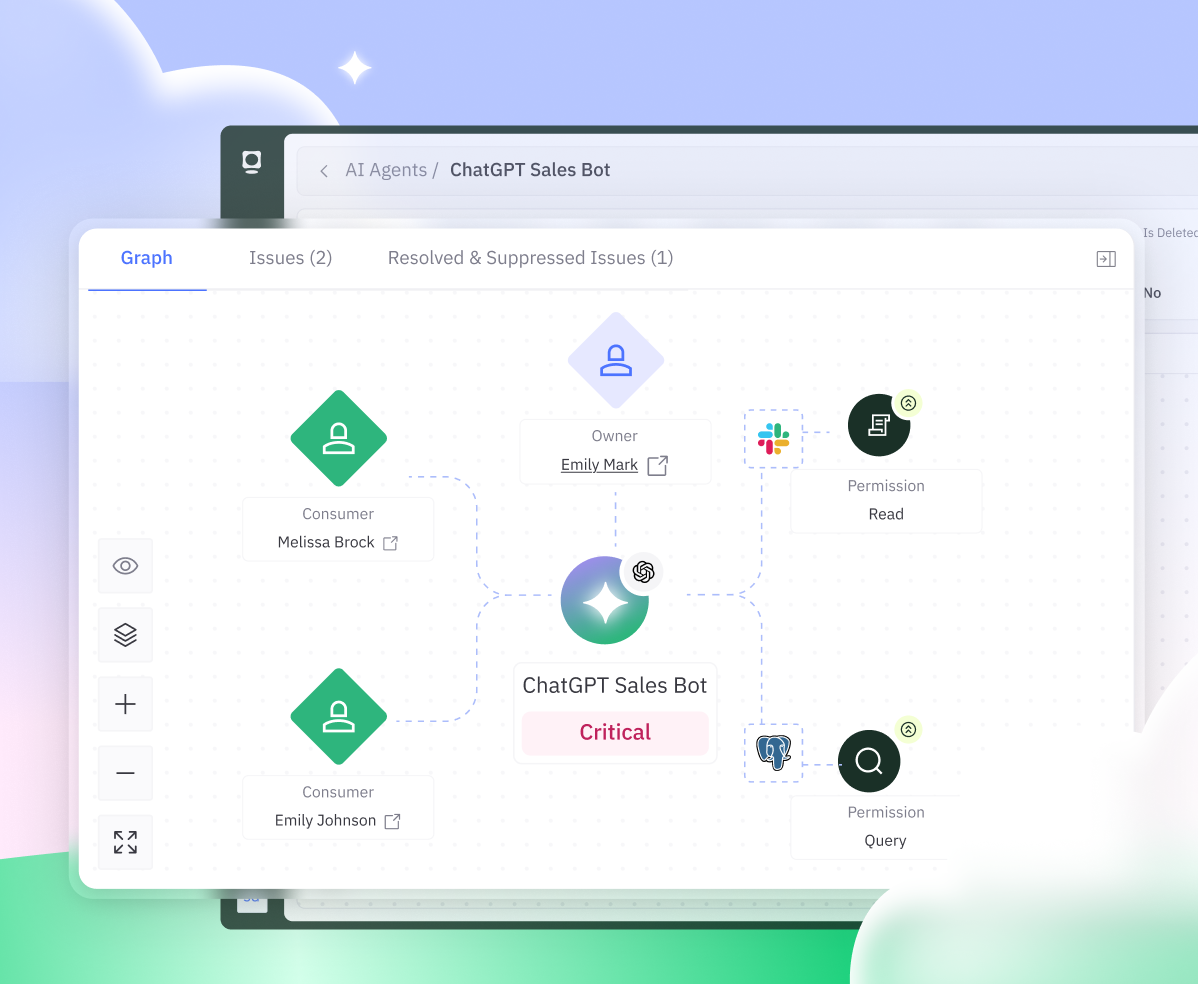
Deep Identity Intelligence
Token correlates AI agents, humans, secrets, permissions, and data in a unified identity graph, revealing the blast radius and enabling remediation at scale.
End-to-End AI Agent Identity Lifecycle Governance
Agents fail over time, not just at creation. Token enforces ownership, intent, access, and governance from an AI agent's creation through retirement.
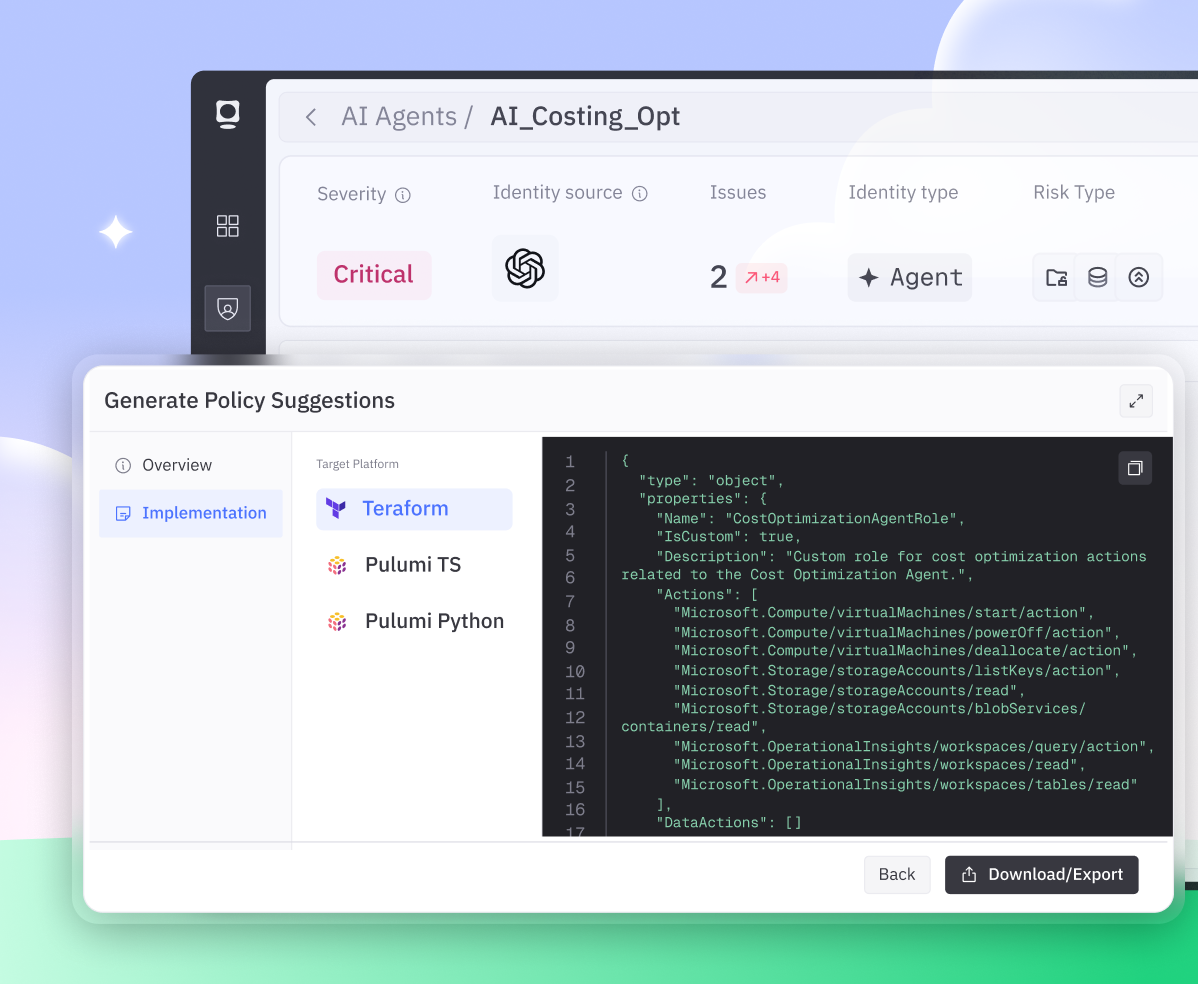
Intent-Based Least-Privilege Enforcement
Token applies intent-aware least-privilege to agents, ensuring they have only the permissions needed for their purpose, and only for the time required.
A machine-first, AI-native approach
Token Security secures every non-human identity — from service accounts
and API tokens to AI agents — with continuous discovery, control, and automated response.
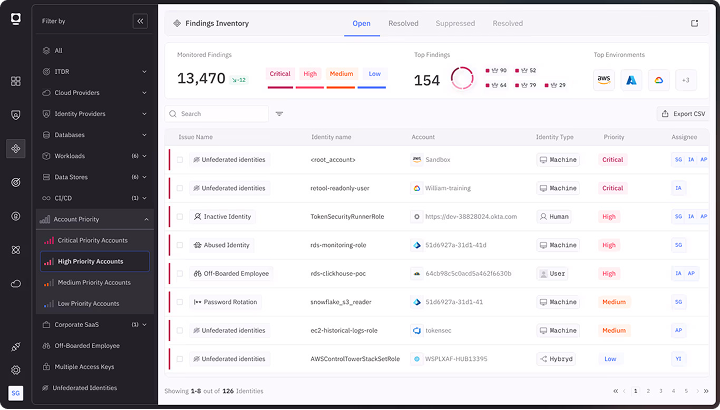
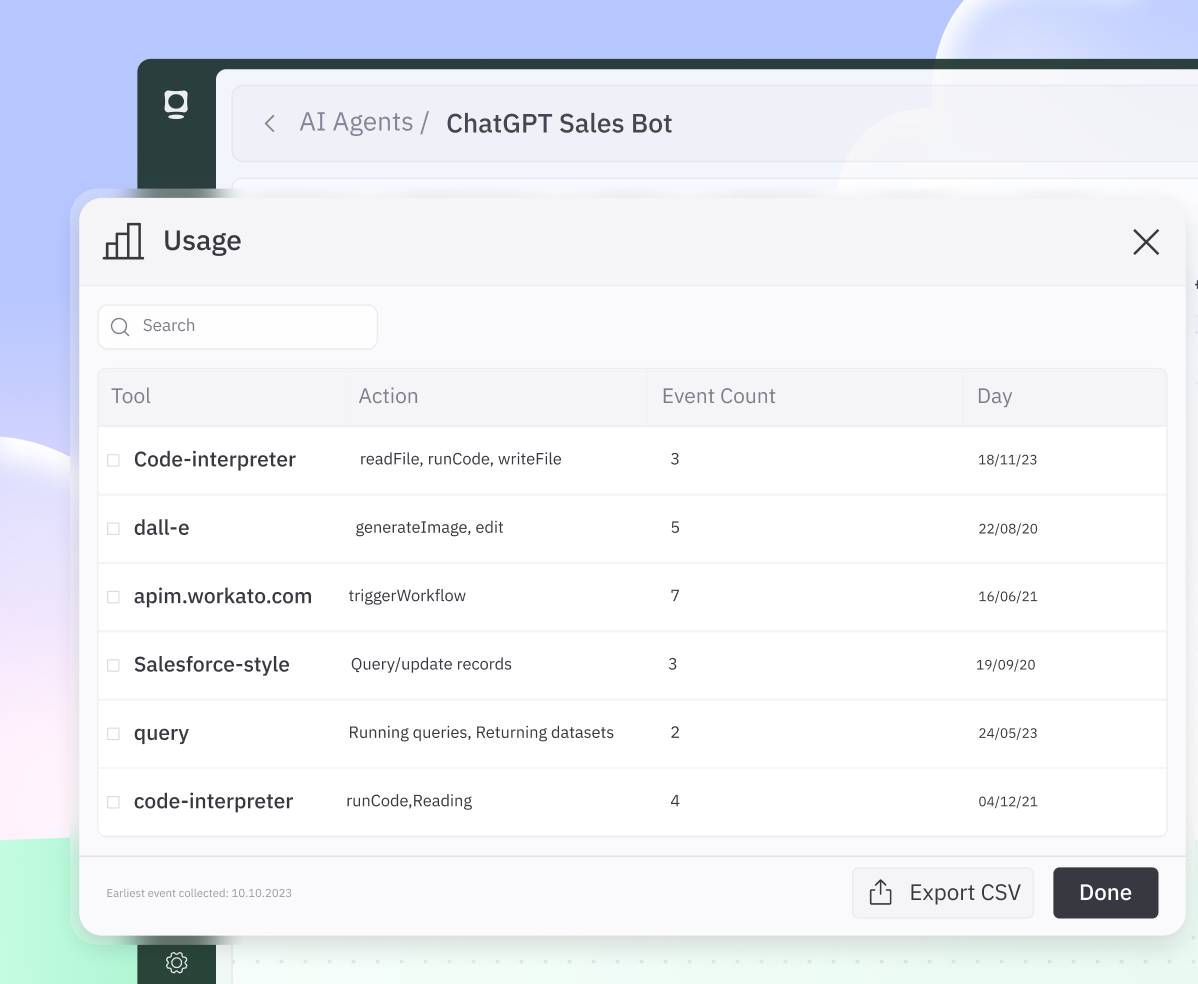
Continuous Discovery & Contextual Visibility
Uncover every AI agent and NHI across
on-prem, hybrid, and cloud environments.


Security Posture Management
Identify permissions drift, right-size access, and eliminate dangerous overexposure.
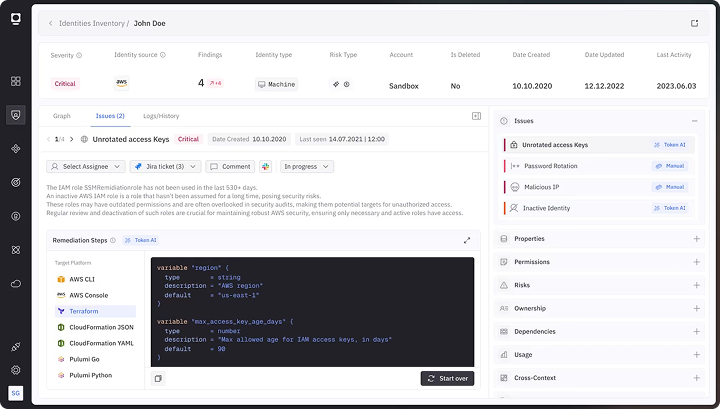
Identity Threat Detection & Response
Detect behavioral anomalies and suspicious activities to respond as they happen.

AI-Driven Automation & Remediation
Trigger intelligent remediation workflows based on dynamic risk thresholds and contextual awareness.
.gif)



.png)




















