Non-Human Identity Management Best Practices
Non-human identities (NHIs)—such as service accounts, IAM principals, machine credentials, workload identities, and autonomous AI agents—have exploded in number, outpacing human identities by orders of magnitude. As a result, non-human identity management is rapidly becoming a core cybersecurity priority
The challenge for organizations is twofold. On the one hand, NHIs are central to modern infrastructure management. These powerful, machine-based identities can be found everywhere, running and managing compute resources ranging from short-lived microservices to long-running services managing critical business operations. Their authentication methods are diverse, including centralized federated identity providers (IdPs), static keys, certificates, and local accounts. On the other hand, the very characteristics that make NHIs useful can result in huge amounts of unmanaged risk for organizations when they aren’t managed effectively.
The unique characteristics of non-human identity management make this challenge even more complex. Legacy identity and access management (IAM) approaches are tightly coupled with the humans they represent. Common management concepts, such as identity lifecycles, investigation techniques, and identity creation and deletion, rely on supplementary systems, such as human resource systems, for context. In contrast, NHIs are typically deployed in context-specific scenarios and task-based activities. They often use entirely different authentication methods and have completely different lifecycle patterns.
This article helps cybersecurity and identity professionals understand how to manage non-human identities. Through a series of best practices, you’ll be provided with practical next steps to help you continue leveraging the unique advantages of NHIs while integrating non-human identity management techniques to minimize the risk they pose to your organization.
Summary of best practices for non-human identity management
{{b-list="/inline-cards"}}
Discover all non-human identities in your system
NHIs are vast in number and are commonly distributed across a large number of components across products and infrastructures. They may be created automatically by orchestration systems, provisioned directly by developers, or generated by CI/CD pipelines. Many NHIs exist for only seconds before disappearing.
However, no matter how vast, complex, or overwhelming this might seem, non-human identity management requires that you know about all of them. Here’s how you can go about it.
Create a non-human identity inventory
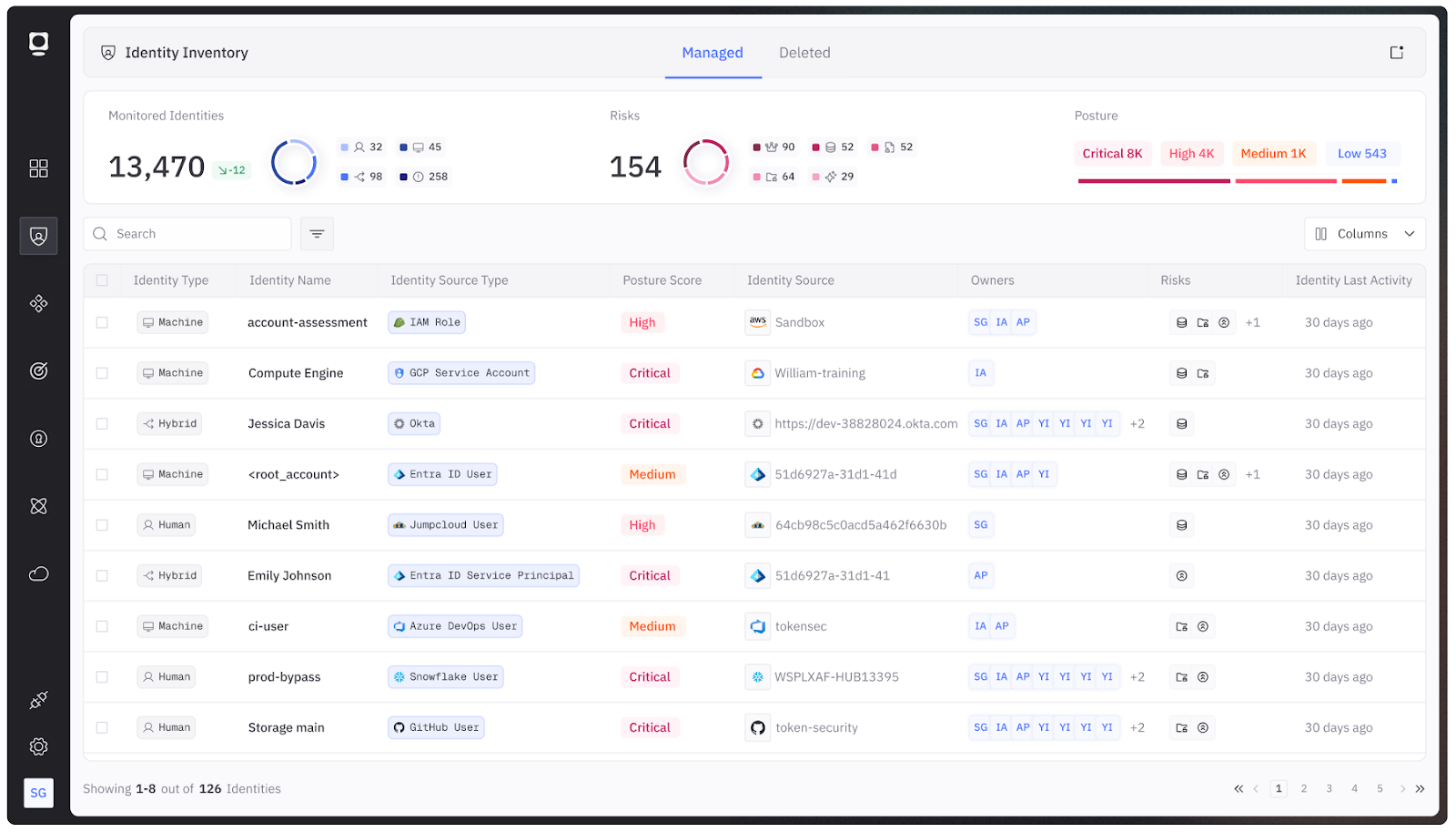
Start by creating an NHI inventory. Ideally, this should be done through your chosen NHI security platform, allowing you to centralize all your NHI analysis in one place. This allows you and your security teams to have an always accurate inventory of the NHIs currently and previously observed in your system.
For instance, the screenshot below is a collation of all the unique NHIs in a system. Each NHI is clearly identified along with supplementary information about it, including owners, risks, and where it is located.
Integrate NHI discovery automation
Once you’ve established an NHI inventory, you need to populate it. Although most security engineers will likely gravitate toward using their existing scanning tools for this approach, it is unlikely to succeed. In almost all instances, legacy tools are designed and built around traditional human identity paradigms rather than the advanced log and metadata analysis combined with contextual understanding and scalability that NHIs need.
To see why this is the case, consider the example of a continuous delivery pipeline that deploys a containerized microservice in a Kubernetes cluster—a routine occurrence in modern application environments. The non-human identities involved in this process include secrets and credentials to access the following systems:
- Code repositories (like GitHub) where the code resides
- Pipeline management tools (such as ArgoCD)
- Kubernetes package managers (Helm chart)
- Kubernetes pod image private registries (such as DockerHub)
- Hosted Kubernetes service providers (such as AWS EKS)
- Databases (e.g., MySQL)
- API keys and tokens that are required to access other microservices or third-party services
- TLS and SSL certificates (for the Kubernetes ingress controllers)
- Object storage services (such as S3)
- Encryption keys for block storage systems (e.g., an AES-256 key)
The application environment could be even more complex. Still, this initial list illustrates why capturing each NHI, metadata, and context, and presenting it in a practical format, is challenging without specialized tooling.
Ensure coverage of all compute infrastructure
Almost every aspect of your computing infrastructure interacts with one or more NHIs. Many of them do so via hardcoded secrets or authentication methods that bypass centralized authentication providers. As a result, you need a way to infer the existence of unmanaged NHIs using a combination of log analysis and deep NHI metadata analysis.
You achieve this by making sure that your NHI security platform integrates with the entirety of your hybrid, multi-cloud computing infrastructure. This includes everything from cloud providers, authentication providers, SaaS products, and on-premises infrastructure. When you do this, you provide your NHI platform with everything it needs to identify these risky NHIs.
{{b-table="/inline-cards"}}
Establish an NHI lifecycle management approach
Non-human identities (NHIs) differ significantly from human identities, and these differences affect how their lifecycles must be managed. Non-human identity management begins with recognizing these differences and acknowledging that NHIs have unique properties that make lifecycle management more complex.
Understand the complexities of non-human identities
To see this in action, consider the two examples of NHIs in the table below.
Each of these NHIs presents distinct risks. The ephemeral NHI is created and destroyed rapidly, with its lifecycle managed by a separate NHI. Non-human identity security professionals would want to ensure that the NHI lifecycle is tightly aligned with the workload runtime, making sure that no unused identities linger once the workload is complete.
In contrast, the second NHI is tightly coupled with the source code. It only exists in the context of the codebase where it is created. Non-human identity security professionals would want to make sure that the links among the developer, codebase, and NHI are tightly monitored. For instance, if the developer leaves, but the credential is still valid (noting general security concerns around having hardcoded credentials in a codebase), then it should be transitioned to a new employee. Alternatively, if the codebase is expired, then the associated NHI must be retired.
Develop an NHI management plan
To manage this complexity, you need to develop and implement a non-human identity management plan. While every organization is different and will use NHIs differently, there are four stages you need to get right, as visually represented in the diagram below:
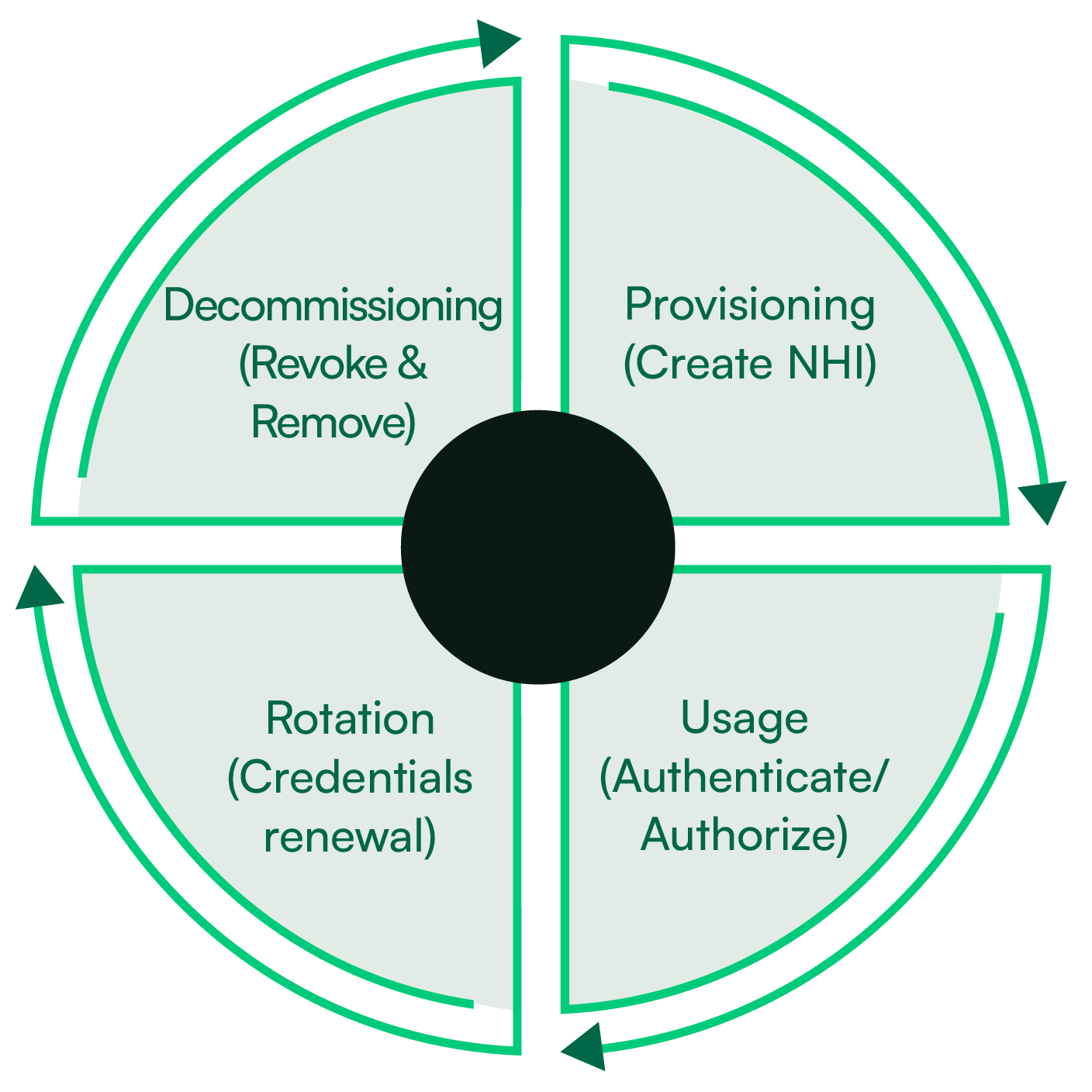
Start with your NHI provisioning. This stage covers everything related to how an NHI is created. For instance, using the two examples from earlier, your process should cover items like how NHIs are managed in codebases and what kinds of checks are made when designing Kubernetes workloads.
Then, develop policies and procedures for managing your active NHIs. Consider how they will be authenticated or authorized while in development and production. Plan for credential rotation on long-lived credentials.
Finally, each NHI's decommissioning procedures should be considered. Plan how NHI permissions should be revoked and how NHIs can be removed from their associated workloads when they are no longer required.
Monitor with a non-human-identity security platform
As you set up your policies and procedures, make sure that you consider how you will monitor for both accidental and malicious noncompliance. This ensures that you and your security team can identify deviations from a secure baseline well before an adversary.
For most organizations, the most effective way to do this is to choose a specialized non-human identity platform like Token Security. This allows you to leverage the platform's deep analytical and operational expertise to improve your NHI security posture rather than investing time and resources to build and maintain it in-house.
For instance, the screenshot below shows a Token Security dashboard that collates all the information about your NHIs together. You can quickly see the number of NHIs you have and where they are in their lifecycle.

Remediate orphaned and unfederated NHIs
Once you have identified all the NHIs in your system, you must remediate any unfederated or orphaned non-human identities. NHIs in an unfederated or orphaned state lack governance, visibility, and lifecycle controls. They do not conform to the discovery and lifecycle practices outlined earlier, so they must be remediated quickly to reduce the risk to your organization.
Understand what orphaned and unfederated NHIs are
Start by understanding what orphaned and unfederated NHIs are.
Unfederated NHIs operate outside of centralized identity management systems. They may use static keys, certificates, or local accounts instead of federated identity providers (IdPs). This makes them harder to monitor, rotate, and enforce with policy.
In contrast, orphaned NHIs no longer have a valid owner or associated workload. Without ownership, they remain active but unmanaged, providing potential unauthorized access to critical services.
Although the causes of orphaned NHIs can vary, a few are listed in the table below.
Map NHIs to workloads and users
Next, map your NHIs to workloads and users. NHIs should only exist when they are required to run a specific, relevant workload, and they are traceable back to a human owner (directly or indirectly, such as through a team or service account manager).
While this sounds straightforward, in practice, it is a complex undertaking. NHIs can exist in many different places, with non-obvious links between them creating a web of complex relationships.
For instance, the screenshot below shows a chain of NHIs that ultimately leads to a high-level project account:
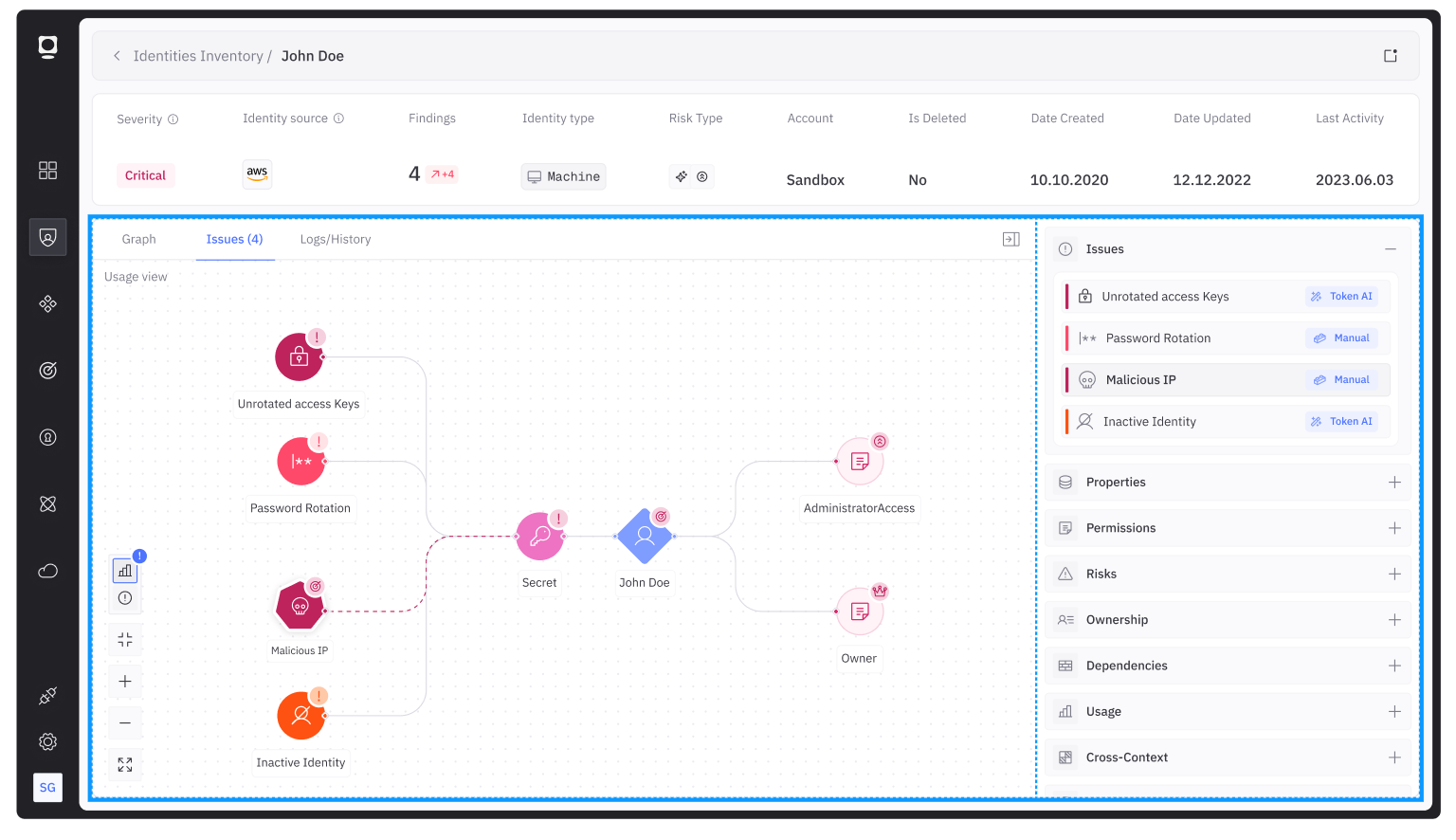
Presented this way, it is easy to see why this would be a problem. However, the underlying analysis required to generate this understanding involves a combination of deep metadata analysis, matching data from multiple log sources, and then combining the results into an overall identity graph.
Rather than getting bogged down in mapping all these relationships, use an NHI security platform to help you. Then make sure it rolls the results of its analysis into a global dashboard.
Remediate risky identities
As you work through the discovery and identity mapping process, you’ll naturally start identifying orphaned and unfederated NHIs. Each of these NHIs represents unmanaged risk to your organization, operating outside your non-human identity management process and creating opportunities for malicious actors to leverage.
Having the right tooling here makes all the difference. Without it, you’ll be stuck searching online for various command-line arguments to remediate your NHI exposure without disrupting your entire system.
A non-human-identity-specific platform like Token Security can help with every step. It can help discover orphaned and unfederated NHIs (as discussed earlier) and provide the steps and commands you need to fix them. Even better, the commands and steps it provides are contextually relevant, saving you many hours of research.
{{b-watch="/inline-cards"}}
Enforce NHI permissions
Like human identities, NHIs must adhere to the principle of least privilege. However, enforcing permissions for NHIs has unique challenges.
Unlike humans, NHIs often interact with systems at machine speed, across multiple services, and at massive scale. Misconfigured permissions can turn a single NHI into a high-value attack vector.
To help your non-human identity management approach get started, a series of practical actions is included in the table below. Each one is paired with a common mistake that organizations make when using NHIs.
As with all things security-related, it is important to pair your best practices with monitoring. This helps you identify issues before they become critical.
For most organizations, the best way to do this is to ensure that their non-human identity platform includes a user-friendly way to highlight when an NHI's security posture is out of compliance.
For instance, the screenshot below shows an inventory of an organization's NHIs, along with easily identifiable areas where they present risk to the organization.

Integrate NHI-specific monitoring
As mentioned, the behavioral patterns, creation processes, and contexts of NHIs are significantly different from human identities, which means you need to integrate NHI-specific monitoring into your environment.
The best way to do this is to ensure that your chosen non-human identity monitoring platform integrates in the areas described in the subsections below.
Analyze API usage specific to non-human identities
First, make sure your NHI security platform integrates API usage. Most NHIs interact with systems through APIs. While this is an increasingly common usage pattern for human identities, the machine-centric nature of NHIs changes what normal, “good” usage looks like.
For instance, most human-centric analysis platforms rely on login frequency as a key indicator of login abuse. However, depending on the NHI you are analyzing, this may be completely normal behavior. Instead, you need to look at unusual or unplanned API calls, such as a build pipeline account suddenly requesting access to production secrets.
Include machine-centric context
Next, make sure your NHI security platform integrates deep NHI metadata analysis. Human IAM monitoring often integrates with HR data (e.g., employment status and leave schedules), but NHIs do not map to this context. Instead, monitoring must rely on technical signals such as workload state, infrastructure telemetry, or IaC definitions. This information is only available in the metadata surrounding the NHI, not through external systems.
For example, while an NHI may operate 24 hours a day (an uncommon human characteristic), an NHI that continues to operate after the associated workload has been terminated is a red flag.
Lifecycle awareness
Finally, make sure your NHI security platform ties into the NHI lifecycle you established earlier. This will ensure that your monitoring takes into account where an NHI is in its lifecycle, as well as the other contextual factors identified earlier.
For instance, in human-centric IAM, a new identity with elevated access is usually a strong anomaly signal. For NHIs, this can be perfectly normal—ephemeral identities are created frequently with specific permissions, some of which will be elevated. However, if the NHI persists beyond its expected lifetime or performs actions outside of its intended workload scope, it becomes an anomaly that should be investigated.
{{b-img="/inline-cards"}}
Conclusion
Non-human identities (NHIs) are now central to modern compute environments, but their ephemeral nature, massive scale, and indirect ownership make them fundamentally different from human accounts.
Organizations must ensure that every NHI is visible, with only the right permissions, and traceable to relevant workloads and human oversight. Doing this at the scale required is a huge task that requires specialized tooling and a clear, systematic non-human identity management approach.
Effective NHI security is not about applying human IAM practices faster. It’s about redesigning identity governance for automation, lifecycle awareness, and machine-speed response, ensuring that every identity is visible, right-sized, and tied to accountable ownership.
.gif)

