Offboarded Employees and the Non-Human Identities They Leave Behind [The Complete Guide]
Offboarded Employees and the Non-Human Identities They Leave Behind
.png)
What Happens to Identities When Employees Leave? Less Than You’d Think
When an employee leaves your company, they typically hand over their laptop and ID badge while their accounts are deactivated. But what about the machine identities they created? The ones that still live in your cloud accounts, CI/CD pipelines, and databases? What about their AI agents?
These Non-Human Identities (NHIs), like OAuth tokens, API keys, SSH keys, and service accounts, often persist long after the employee has left the building. And in many organizations, there’s no clear ownership or process to track, transfer, or revoke them.
The question is, for how long?
Best intentions are that organizations revoke system access to employees on the day they leave. But, 53% of IT leaders are terrified by the risk of a cyberattack through an unmanaged account when an employee is not properly deprovisioned. This includes their NHIs that continue to lurk in cloud environments, IdPs, GitHub repositories, or SaaS apps.
In this blog, we'll explore the key challenges of offboarding employee NHIs, along with an actionable, step‑by‑step guide to making the transition process both smooth and secure.
Four Reasons Why Orphaned NHIs Are a Growing Threat
Lack of Ownership & Accountability: NHIs are everywhere, and many of them don’t have defined owners. Insufficient governance and oversight were found to be exacerbating the risks associated with machine identities. A surprising 75% of companies reported having machine identities without dedicated personnel managing them, increasing vulnerabilities to data loss and compromised access. Human user accounts have formal offboarding policies, workflows, and HR processes. The same cannot be said for NHIs, which are often created by code, scripts, pipelines, automation tools, and AI agents. And once created, they often go untracked. These unmanaged NHIs expose the organization to significant cybersecurity risk.
That same employee might have access to multiple shared accounts whose credentials aren't rotated each time someone leaves the organization. That same employee might have also created a large volume of NHIs that continue operating after the employee's accounts were revoked, and the employee might still have access to the credentials they created for those NHIs.
Without clear ownership or NHI lifecycle management, an organization has almost no visibility into where these identities reside or what resources they can access. Transferring ownership becomes exceptionally complex when there is no attribution for these accounts, so those NHIs often remain active indefinitely, creating a hidden attack surface.
Decentralized Identity Management: NHIs are scattered across many environments without any governance, making it nearly impossible to track, secure, and deprovision effectively. Consider the use case of an M&A, where many employees may be released due to mass layoffs. The acquiring company inherits countless service accounts, many of which have no clear owners or assigned roles.
Traditional IAM solutions weren’t designed to govern machine identities, which presents a real challenge for enforcing consistent access control policies across all environments. Centralized NHI lifecycle management becomes critical because, without it, there’s no way to know which accounts are still active or who has access to them. You can’t secure what you don’t know exists.
AI Agents and Automation Risks: According to a recent Capgemini survey, 82% of 1,100 executives at large enterprises plan to integrate AI agents within the next three years.
But they also pose a serious risk for NHIs if left unmanaged or without identity governance.
AI agents can introduce new security risks that are outside of the organization’s scope for an offboarded employee, since they may have a small army of AI identities without any clear ownership. That’s assuming you have an idea of how many AI identities were created by that employee, and where they operate. Can those AI agents still trigger automations on Jira for example? If that NHI is left active after offboarding, it could continue to run automations on incorrect logic using stale permissions. A security incident tied to an AI agent could escalate within seconds
Excessive Permissions: NHIs are over-privileged and under-monitored. NHIs in cloud environments with admin access can easily bypass security policies since there is no automated access review process. If cloud permission sets aren't controlled, those NHIs can delete databases, overwrite objects, or drive up costs for unauthorized EC2 instances in AWS or Azure VMs. Even if these permissions are audited and managed periodically, once an employee leaves, the identities they managed still maintain those permissions - even if they aren’t required anymore at some point in the future.
And then there's the risk of cloud misconfigurations, which can expose terabytes of sensitive data to public environments if security guardrails aren't enforced.
And who is managing those permissions? Is it a trusted internal security lead or a third-party provider that has minimal insight into the organization's employee lifecycle? If those excessive permissions aren’t revoked quickly, an attacker could escalate permissions in cloud environments and trigger a massive breach.
How to Make the Employee Offboarding Process a Smooth Transition
You can’t treat NHIs like an afterthought. As AI adoption surges, they now outnumber humans by as much as 45:1. It’s time to extend offboarding to every machine identity your employees own and manage.
Establish Clear Policy Guidelines for Employee NHI Offboarding. HRIS systems are only capable of tracking and managing human identities, so security teams must:
- Review existing offboarding policies regularly to ensure compliance and that any new tools or platforms introduced into the environment are documented.
- Ensure that the policies cover AI models and integrations, such as AI Agents, Large Language Models (LLMs), and Model Context Protocols (MCPs), which might continue to operate with the employee’s unmanaged identities or stale tokens, potentially triggering unauthorized automated workflows and exposing sensitive data.
- Apply network restrictions to all NHIs to prevent external access by offboarded employees outside the organization's network
Discover Every NHI and Reassign Ownership
- Map and inventory all NHI accounts, API tokens, SSH keys, and cloud roles that belong to or were created by that employee
- Automatically assign NHI ownership to the appropriate individuals and inform them of their new accounts and responsibilities.
- Delegate a team lead who will resume ownership of the employee’s remaining accounts and identities once they’ve fully offboarded.
Rotate Credentials and Revoke Access
- Revoke all employee credentials immediately after their departure to prevent unauthorized access. This includes rotating API keys, passwords, OAuth tokens, and secrets that the employee created during their tenure in the organization. Developers might have duplicate keys embedded in CI/CD pipelines or GitHub repositories that attackers can exploit through credential stuffing or by introducing malicious packages in open‑source dependencies.
- Identify exposed credentials that may be found in productivity tools, such as Slack or Jira, where machine identities can maintain access to private channels, download files, or read sensitive conversations. Avoid long-term credentials, and use temporary credentials for NHI authentication to reduce the risk of leaked secrets being exposed.
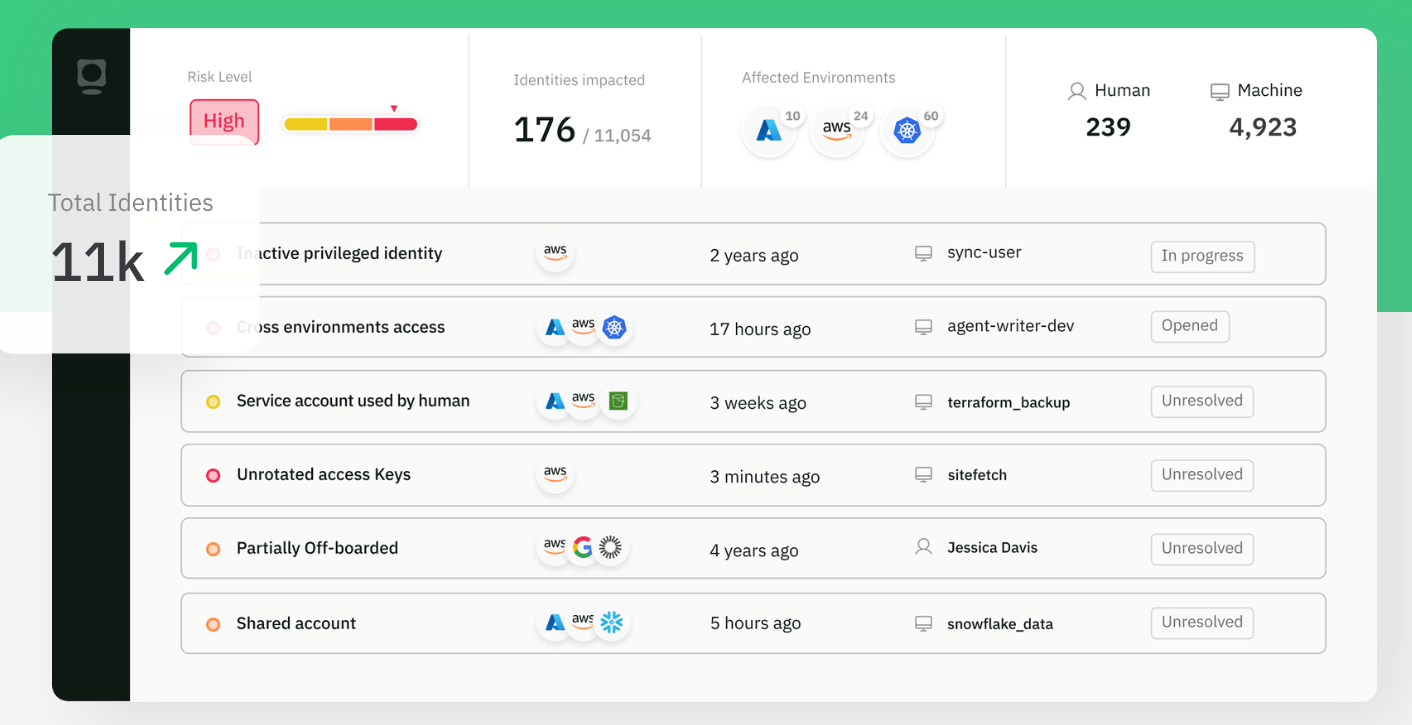
Automate Employee Offboarding with Machine-First Identity Security
Token Security creates a comprehensive and contextual map of all machine and non-human identities that exist in your cloud, on-premises, and AI environments that can access your systems. Token Security provides total visibility and ownership of all discovered NHIs across affected environments to help security teams prioritize remediation decisions based on contextual understanding. Additionally, the NHI Risk Graph™ provides visualization of NHI risk dependencies to ensure confident remediation.
With Token Security, you can revoke excessive permissions, govern identities, deprovision stale accounts, and establish clear accountability for every NHI in your organization with machine identity lifecycle control. Make the employee offboarding process a smooth and secure transition with Token.
Schedule a demo today.
.gif)
%201.png)





