Best Practices for Managing Non-Human Identities | Token Security
Non-human identities (NHIs) far outnumber human users across most modern enterprise environments. They enable API integrations, power CI/CD pipelines, underpin infrastructure-as-code (Iac) provisioning, orchestrate containerized workloads, harden cloud services, and enable AI agent workflows.
These powerful digital actors are the backbone of all modern infrastructure systems, constantly accessing every corner of cloud, application, and AI environments using service accounts, API keys, OAuth JWT tokens, database credentials, Linux root accounts, digital certificates, or private cryptographic keys.
However, unlike human users, they sprawl quickly and are challenging to discover, contextualize, and manage. They are more often than not provisioned without coordination, granted overly permissive access, and untracked across their lifecycle. Consequently, they are among the most exploited attack surfaces.
This puts organizations in an untenable position. On the one hand, modern computing paradigms require NHIs to operate; on the other hand, they pose an emerging critical cybersecurity risk.
This article explains how to manage NHIs effectively at scale. Using a series of best practices, you’ll be shown practical ways to manage secure non-human identities across your hybrid, multi-cloud infrastructure while minimizing disruption and reducing risk.

The best practices for managing non-human identities
Discover non-human identities at scale
Identifying non-human identities at scale faces two major challenges: their overwhelming quantity compared to traditional human identities and the difficulty in determining whether a non-human identity is securely managed.
To understand the scale of this challenge, consider this: in some organizations, the ratio of NHIs to human identities exceeds a hundred to one. Furthermore, in a well-secured environment, every single non-human identity would be connected with a relevant workload or service. Each NHI would only have the necessary access to perform its specific task, and ultimately, it would be possible to associate any given NHI with a real, current human identity.
Of course, most organizations are far from this ideal and are looking for practical ways to mitigate this risk. If that’s you, read on to discover the three steps you can take to remediate this situation and begin developing an accurate, comprehensive NHI inventory.
Integrate NHI-specific analysis
NHIs have completely different patterns of life compared to legacy IAM services to manage human users, and you need to treat them as such. Without this awareness, you will never be able to identify NHIs at the scale and accuracy you need. Start, then, by integrating non-human identity-specific analysis into your cybersecurity processes.
Although you could theoretically build this capability in-house, this would take many years and a significant portion of your budget. It is far more complex than just ‘downloading some logs and building a Python script’ and for most organizations, this level of investment is impractical.
A better approach is to leverage the deep technical expertise and accumulated experience from an NHI security-specific platform like Token Security. Leveraging specialized technology allows you to focus on building your NHI inventory, rather than getting bogged down with the overwhelming task of maintaining in-house scripts.
Integrate with all infrastructure
Next, make sure your NHI platform integrates with the entirety of your known infrastructure.
Consider an NHI using a static credential to authenticate and see why this is necessary. In this scenario, the only record of the NHI operating will be from task-based logs. There will be no regular authentication checks with a centralized IAM service, with knowledge of it, and depending on where the NHI originated, there may be no record of the NHI ever being created.
Integrating with your entire tech stack is the only practical way to address this challenge. You need to go beyond standard IAM and SIEM integrations and consider all the other aspects of your tech stack, including cloud service providers, CRM platforms, Automation Platforms, and so on.
In addition, make sure that your chosen non-human identity security platform comes with a wide range of out-of-the-box integrations to discover NHIs in environments such as AWS, GCP, Azure Entra ID, Google Workspace, Active Directory, Okta, Salesforce, Snowflake, and much more. This will not only future-proof your NHI platform but also ensure that you can integrate any previously unknown yet additional services your NHI discovery platform identifies.
Ensure continuous detection
Finally, ensure that your NHI discovery platform uses continuous discovery for its analysis. Many NHIs exist for brief moments, waking up to execute a single task or workload, before shutting down until the next event is triggered. The only way to capture and discover NHIs operating this way is if your NHI platform is continuously ingesting and analyzing your organization's tech stack.
Create an identity risk graph
An identity risk graph allows you to visualize an inventory of all your NHIs and their relationships to their human owners, resources, services, privileges, secrets, and risks. Having one at hand allows you to quickly identify areas of over-provisioning, understand interconnections and dependencies, establish the organizational context in which they operate, and respond rapidly in the event of a cybersecurity incident.
For instance, consider the screenshot below:
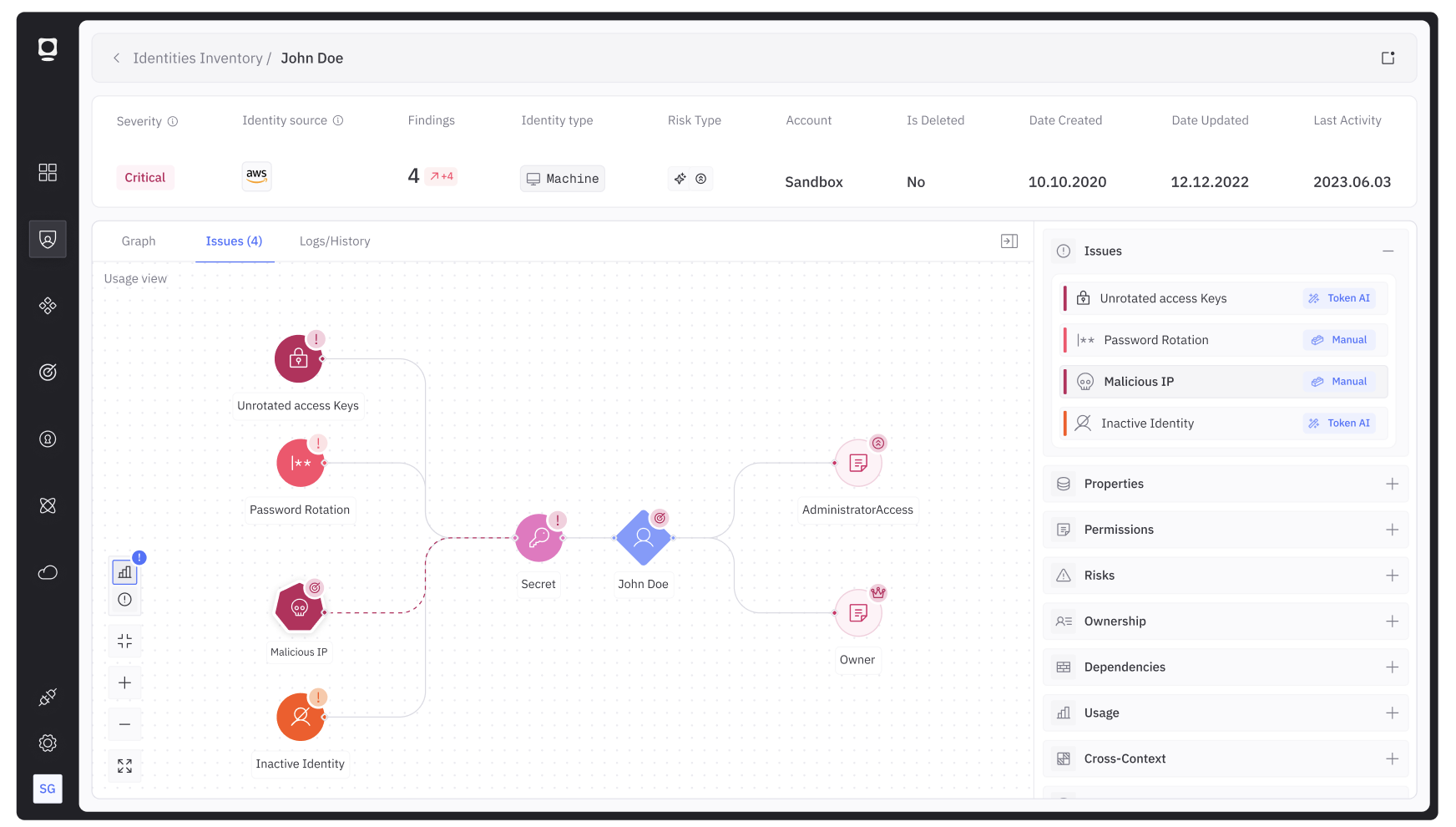
In this screenshot, you can clearly see an entire chain of NHIs that shows the human owner, an issue with a secret, and what services are dependent on the secret for access. Cybersecurity professionals would be interested to observe things like:
- Who the human owner is and what the NHIs have access to
- What the impact is from an expired secret
- A series of ‘High Risk’ annotations against several accounts
Although the utility of an identity risk graph is obvious, creating one requires several ingredients. Each ingredient is a specialized area encompassing advanced metadata analysis, contextual input from policies and known attack vectors, and, in some cases, vendor-specific algorithmic analysis.
Rather than attempting to recreate this from scratch, most organizations should ensure that their chosen NHI-security vendor includes this capability in their toolset.
Manage all non-human identity lifecycles
Although non-human identities are very different from traditional human identities, each one still follows a distinct lifecycle that should be closely monitored and enforced.
For instance, consider a fairly common orphaned NHI scenario. An engineering team issues a deployment token for a GitLab CI/CD pipeline to manage infrastructure updates. Eventually, this system is decommissioned, and the team migrates their workloads to a new cloud platform. However, the token is never revoked.
Because the original workload is considered decommissioned, it continues to exist, with all its original privileges, without active monitoring. During a security assessment, red teamers identify the stale token and demonstrate how it could be used to modify infrastructure outside the approved pipeline.
Establish an NHI lifecycle governance process
The first step to solving this scenario is effectively managing your non-human identity lifecycle. You do this by establishing an NHI lifecycle governance program that defines how NHIs will be handled.
Most organizations will have predefined management programs they can leverage to do this. However, if you don’t, here is an example of what this could look like at the NHI level.
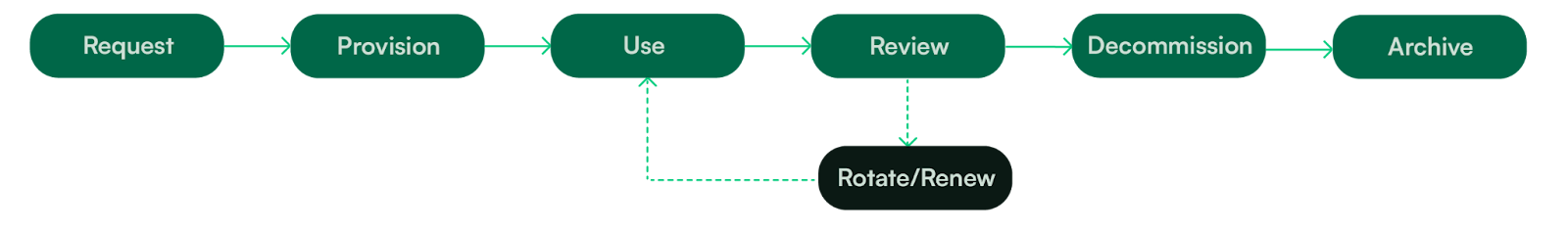
First, start with a request that captures a desired NHI's purpose, owner, and time bounds. Then, once approved, provision the NHI and allow it to be used. On a set cadence, automatically review it, and validate that its usage still matches its intent. If the identity continues to serve a valid purpose, extend its lifespan, or rotate it to refresh its credentials. If not, move it toward decommissioning, where access is revoked, and then into archival for audit and compliance.
Visually, this would look like the diagram below:
Feed into your NHI management system
Once you’ve established this process, use it to feed contextual data into your overall NHI management processes. This lets you associate metadata information like ownership, purpose, and time bounds with the NHIs.
For instance, in the process above, the owner of the created NHI was clearly identified at the time of the request. Knowing this information, you can create a process that allows you to:
- Transfer ownership of the NHI in the event of the person leaving
- Route requests for information that require human input
Trust by verify
Finally, integrate NHI monitoring into your cybersecurity and IT processes. Even the most robust processes can experience issues, and the best time to identify them is before an adversary does. Use your chosen NHI-security platform as an independent verifier, and configure it with alerts to let you know when things aren’t going well.
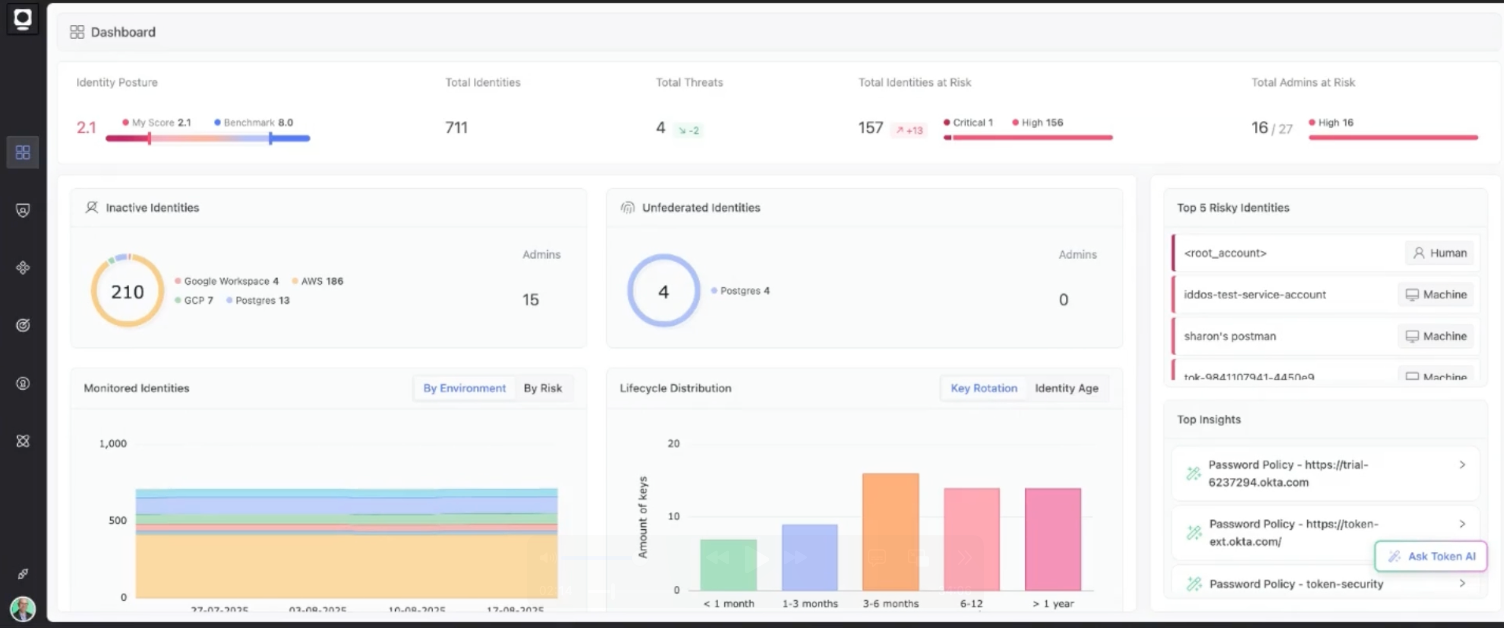
Some of the key things you should monitor are:
- The total number of NHIs that are being tracked
- How long since each NHI credential was last rotated (typically grouped up into time-based buckets)
- Any unfederated or orphaned identities
- Any identities that are at risk
Here’s an example of what a dashboard containing such information could look like:
Integrate intelligent remediation
Most cybersecurity professionals have experienced the gut-wrenching feeling of watching their ‘perfect’ security remediation run headlong into operational disruption. That moment when they realize that their ‘simple command-line argument’ managed to brick a supercritical business server. Or, even worse, it didn’t even achieve its desired security effect, and so was functionally useless.
When remediating the high-risk credentials your discovery process is unearthing, avoid this outcome by using the three steps below.
Gather context using your identity risk graph
Start by leveraging your identity risk graph. This map gives you holistic insight into all the identities and services your target remediation NHI will impact. With a few clicks, you can quickly identify things like the downstream identities and workloads dependent on the NHI in question and the owners associated with them. With this step, you can do a quick sanity check on your planned approach, or even better, reach out to any potentially impacted owners and co-develop a solution with them.
Leverage your NHI-platform remediation capabilities
When remediating an NHI vulnerability, avoid Googling (or OpenAI’ing) to find a Terraform, AWS CloudFormation, or Kubernetes command-line argument, as operations teams often do when in a rush. This approach is almost guaranteed to cause service disruptions and is impractical at scale.
Instead, leverage the intelligent remediation capabilities of platforms designed for NHI remediation. This allows you to de-risk the remediation step while gathering the contextual information mentioned in the first subsection. Token Security takes this one step further and recommends contextually relevant command-line arguments and clear remediation guidelines to achieve the desired outcome.

Tackle the highest risk identities first
While any unmanaged or orphaned NHI represents risk to an organization, in most cases, not all of these risks are equal. Once you’ve adopted an NHI management platform, start by analyzing and remediating the NHI associated with your highest risk applications.
Do this by working through a prioritized list of your vulnerable NHIs. In most cases, your NHI security platform will do the prioritization for you, allowing you to focus on doing the actual remediation.
Extend intelligent remediation to routine secrets rotation
Although this section focuses on intelligent remediation, most practical aspects can be easily applied to general NHI hygiene activities. For instance, most long-lived NHIs require routine secrets rotation as part of their lifecycle management. The steps involved in doing this are similar: establish context, avoid risky command-line arguments, and rotate the highest-risk credentials first.
Unless you have organizational constraints otherwise, you should use your NHI analysis platform to assist with this task.
Enforce least privilege and context-aware access
So far, this article has covered many of the concepts normally covered under identity security posture management (ISPM). However, one more concept must be covered: the principle of least privilege and its more advanced form, context-aware access. This is one of the most effective ways to reduce the risk from NHIs, and it is also one of the hardest things to implement and monitor.
You now have all the building blocks to implement this effectively.
Integrate least privilege into your policies
Start by integrating processes related to privilege management into your policies. An earlier section introduced an NHI lifecycle process, which started with a simple request that captured an NHI's purpose, owner, and time bounds.
Expand this process to include active controls around how, where, and why privilege is provided. Require extra permissions for highly privileged accounts or apply additional controls for a given level of access. Reinforce these controls by actively refusing permission requests that do not include this information.
Add context-aware access
Next, apply context-aware access controls to your NHIs. Context-aware access restricts the ways a given NHI can be used once deployed. For instance, an API token might only be available during deployment windows, or a workload identity is only trusted when deployed from a specific subnet.
You can do this by adding policies to your NHI lifecycle governance process and enforcing them in your tech stack. While it may not work for all NHIs, doing it everywhere you can narrows their risk profile, making it harder for malicious actors to use stolen identities against you.
Use advanced NHI-specific monitoring tools
Procedurally limiting the amount of privilege each NHI has, and the context in which it operates, is all good and well; however, no system is perfect, and it only takes one compromised NHI to let adversaries in.
You mitigate this risk by including an advanced, NHI-specific monitoring platform in your cybersecurity order of battle. This platform should have all the characteristics previously discussed in this article, such as complete integration into your compute stack, the ability to develop accurate identity maps, and an analytics approach that dives deep into each NHI's metadata. It should also include the ability to send real-time notifications when a newly provisioned NHI fails to comply with the governance policies.
Prepare for Identity Threat Detection and Response
No matter how thorough your preparations or how robust your NHI management processes are, you must always be prepared to respond to identity-related security incidents. You do this by preparing for Identity Threat Detection and Response (ITDR).
ITDR is a cybersecurity discipline specializing in identifying and responding to identity-specific threats. While it often complements other cybersecurity capabilities, it is its own specialization with its own nuances.
For instance, if an endpoint detection and response (EDR) tool identifies a malicious process spawning multiple threads, an ITDR solution would provide deep context around the human or non-human identity responsible for starting the process. Assuming you have set up your identity risk graph, an ITDR solution can map the identity chain back to the account that was compromised initially.
Implement the steps below to prepare for ITDR:
Final thoughts
As infrastructure scales, AI is rapidly adopted, and automation becomes the default, non-human identities are now outnumbering human accounts by orders of magnitude. When left unmanaged, these identities create one of the most pervasive and least visible attack surfaces in enterprise environments.
Don’t ignore the vulnerabilities exposed by NHIs; instead, implement the practical steps discussed in this article to protect your cloud, workload, application, and AI environments. This means going beyond a superficial measure using in-house scripts to catch orphaned or shadow NHIs, and instead integrating powerful analytics tools combined with industry best practices.
When you adopt the best practices described in this article, you will find that you can drastically reduce your organizational risk without slowing down innovation, and while strengthening your identity security posture management.
.gif)
%201.png)





