New AI Security Guide Provides a Maturity Model for Secure Agentic AI Adoption

As enterprises rapidly adopt AI agents to drive innovation and efficiency, one critical question remains unanswered: How do we ensure these autonomous systems are secure, governed, and trusted?
Today, Token Security, together with Descope, is launching The AI Security Guide: A Maturity Model for Secure Agentic AI Adoption. This guide offers a practical framework co-developed by leading CISOs, security architects, and identity experts to help organizations adopt agentic AI safely, securely and strategically.
Why Is This Guide Important?
82% of enterprise leaders plan to deploy AI agents in the next three years. Yet most organizations remain dangerously underprepared to manage the security implications of autonomous AI systems. Unlike traditional AI tools, agentic AI can plan, decide, and act independently, interacting with services, APIs, systems, and sensitive data without direct human supervision. This shift from reactive tools to autonomous actors significantly expands the attack surface, introducing new identity, access, and governance challenges that existing security models were never built to handle.
This shift introduces entirely new risks:
- Autonomous misbehavior that could trigger outages or policy violations
- Non-human identities (NHIs) that operate without oversight or traceability
- Unstructured access to enterprise systems via OAuth, plugins, or shell commands
- Regulatory exposure from identity gaps, shadow AI, and model misuse
Enterprises are moving fast with AI deployments to gain competitive advantages. But without the right controls, innovation can quickly become a liability.
What’s Inside the Guide
The AI Security Guide offers a phased maturity model designed to help CISOs, security professionals, and enterprise IT leaders embed security into every stage of AI adoption without impacting innovation. As organizations move beyond isolated pilots to autonomous, agent-driven systems, security can no longer be addressed with disconnected point solutions or one-off controls. A maturity model provides a structured, progressive path—aligning identity, access, governance, and visibility as agentic AI capabilities expand—so security scales intentionally alongside autonomy. Here are the phases of the maturity model:
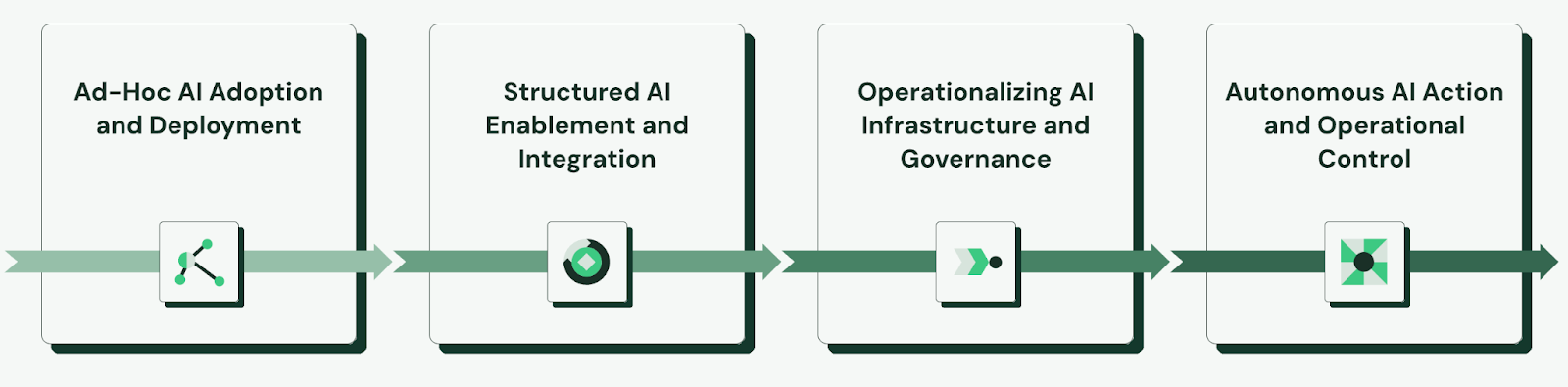
Phase 1: Ad-Hoc AI Adoption and Deployment
Ultimately, this initial phase is less about halting AI experimentation and more about creating visibility and laying the groundwork for structured growth. By identifying where AI is already in use and by implementing basic controls, organizations can reduce risk exposure and prepare for structured adoption.
Phase 2: Structured AI Enablement and Integration
This phase focuses on establishing a foundation for scalability. With consistent access controls, NHI governance, and formal tool onboarding, enterprises can harness the full productivity benefits of AI tools while maintaining visibility, traceability, and control. Structured integration enables AI to become a secure, scalable part of daily operations and prepares the organization for the next phase.
Phase 3: Operationalizing AI Infrastructure and Governance
This phase empowers organizations to unlock competitive differentiation through proprietary AI capabilities while maintaining control, trust, and transparency. By deploying a secure MCP server and enforcing strict governance, enterprises can scale internal model development with confidence. This foundational structure not only reduces risk, but also enables seamless advancement to the next phase.
Phase 4: Autonomous AI Action and Operational Control
This phase delivers the full promise of secure AI: action without delay, insight without bottleneck, and execution at scale. However, it also demands a reimagined approach to identity, access, and trust. With structured governance, scoped privileges, and full observability, autonomous agents can safely and securely become operational teammates to maximize efficiency, while preserving accountability and control. Enterprises that master this phase will lead the next era of intelligent, adaptive, and resilient AI operations.
Alongside the maturity model, the guide also provides:
- A framework for cross-functional security controls (IAM, data privacy, model governance)
- Tactical guidance on securing MCP, A2A protocols, and OAuth integrations
- A business case for AI agent identity as the new foundation of enterprise security posture
- Real-world examples and risk scenarios for every maturity phase
Who Is the AI Security Guide for?
- CISOs seeking to build trust in AI systems before they scale
- IT and IAM teams managing a surge in non-human identities
- AI/ML platform teams responsible for deploying internal models and agents
- Security architects implementing policies, controls, and guardrails for AI implementations
- Executives and boards who want confidence that their AI investments are secure, compliant, and resilient
The Bottom Line: Secure AI Is Scalable AI
Agentic AI will redefine how work gets done—but only if security, identity, and governance keep pace. The AI Security Guide is the blueprint for getting there.
Access the full guide and begin your journey to trusted, enterprise-grade AI adoption. https://secureaiguide.com/
Let us know how you’re using the guide, or reach out if you’d like help applying the maturity model in your organization. Sign up for a demo of the Token Security platform
Security isn’t the cost of AI adoption. It’s the catalyst for doing it right.
Co-developed by Token Security and Descope, with contributions from security leaders at Silicon Valley CISO Investments (SVCI), Vercel, Verily, AppLovin, Live Oak Bank, Notable Capital, and more.
For cybersecurity professionals located in the San Francisco area, Token Security and Descope will be hosting an exclusive Agentic AI Security Dinner on August 27, 2025. The event will gather security leaders, CISOs, and innovators to discuss best practices, emerging challenges, and real-world implementation of secure Agentic AI.
RSVP now: https://lu.ma/Dinner-aug27-2025
.gif)
%201.png)