ITDR for NHIs: How Token Security Detects Risky Behaviors and Materialized Threats
.png)
As identity becomes the new perimeter, Identity Threat Detection and Response (ITDR) is emerging as a critical capability, especially when it comes to the complex environment of Non-Human Identities (NHIs). These machine-based identities, such as service accounts, APIs, cloud workloads, and AI agents, are exploding in scale and privilege, yet remain poorly governed by legacy security tools. Token Security is changing that.
In this blog, we explore how Token Security reimagines ITDR for NHIs, focusing on detecting both risky behaviors and materialized threats, based on deep, real-time identity usage data.
The Unique Challenges of ITDR for NHIs
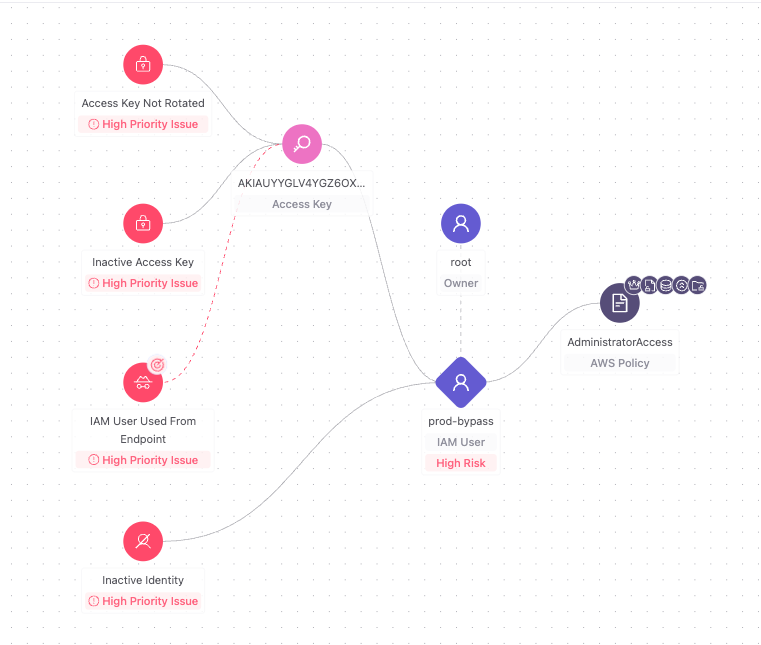
Traditional ITDR was built around human identities for employees whose credentials might be compromised, whose accounts might behave abnormally, and for whom remediation is relatively straightforward (disable an account, force an MFA challenge, etc.).
However, NHIs are different:
- Scale: There are often tens of thousands to hundreds of thousands of NHIs in an organization, which is an order of magnitude more than human users
- Privilege: NHIs frequently have broad, unrestricted access to critical infrastructure (services, applications, AI systems, databases, CI/CD pipelines)
- Persistence: NHIs often rely on long-lived credentials that don’t rotate frequently, increasing the window of vulnerability
- Remediation Risk: Disabling a compromised NHI can unintentionally break production systems or revenue-generating workflows
In short, NHIs are high-privilege, high-risk, and hard to remediate. That means ITDR for NHIs must be more precise, automated, and context-aware.
Token Security’s Four Pillars of NHI Security
Token Security’s NHI security strategy is grounded in four core defensive layers:
- Lifecycle Management: Ensures NHIs are properly created, rotated, and decommissioned with context-aware workflows
- Security Posture Management: Monitors misconfigurations like unrotated keys, overprivileged roles, or long-lived credentials
- Risky Behavior Detection: Identifies usage patterns that deviate from the norm but are likely still internally initiated
- Threat Correlation and Anomaly Detection: Links identity activity to external threat intelligence and behavioral anomalies
Token Security enables security teams to discover, understand, govern, and protect
NHIs, while detecting and responding to emerging threats.
Detecting Risky Behavior Before It Becomes a Threat
The Token platform is built on the philosophy that:
99% of anomalous identity events are false positives. Of the 1% that are real, most are risky behaviors, not active threats.
That means effective ITDR isn’t just about “stopping attacks.” It’s about surfacing and addressing operational shortcuts, policy violations, and unintentional exposure by internal users or processes.
Some real-world examples that Token Security can detect:
- A developer copying a service account credential to their laptop and triggering alarms meant for attackers.
- A staging NHI using a production-level role is often the result of corner-cutting, not a malicious actor.
- Credential usage outside approved time windows or from unexpected geographic locations.
By understanding who the identity is, who owns it, what systems it touches, and how it behaves normally, Token Security surfaces these behaviors early and accurately.
Materialized Threats: From Risk to Response
While risky behavior dominates detection volumes, Token Security also flags true materialized threats, such as unauthorized access by a third party or abuse of leaked credentials.
However, the response to threats and remediation for NHIs is complex. Disabling a database credential used by a customer onboarding service could halt a revenue generating application. This is why Token Security takes a contextual, data-driven approach for intelligent response:
- Maps NHIs to business impact: Not all NHIs are equally critical. Token Security identifies and helps prioritize the NHIs that pose the most critical risk to organizations
- Enables surgical remediation: Pinpoint scope of compromise to avoid breaking mission-critical workflows
- Supports external integrations: Connects with SIEMs and threat intelligence tools to correlate detections with wider security ecosystems
Detection Powered by Real-Time Usage
Token Security’s core differentiator is its data layer: a real-time graph of NHI usage across fragmented identity sources (cloud infra, CI/CD, SaaS apps, microservices, AI agents). This allows Token Security to detect threats even when identity infrastructure is decentralized and credential stores are siloed.
Where traditional ITDR struggles with fragmented signals, Token centralizes and contextualizes them enabling powerful detection at scale.
Final Thoughts: ITDR That Works for NHIs
As organizations scale into tens of thousands or more of NHIs, legacy identity security solutions can’t keep up. Token Security fills this gap with an ITDR solution purpose-built for NHIs that is focused on detection accuracy, intelligent response, and usage-driven visibility.
If you're ready to detect risky behavior before it becomes breach material, and respond to threats without breaking your business, it’s time to take a closer look at Token Security.
Want to see Token Security’s ITDR capabilities first hand? Request a demo or contact our team today: https://www.token.security/book-a-demo .
.gif)









