IP Hardening in the Real World: A Story from the Trenches
The Moment We Found It
It was the kind of finding that makes you sit up in your chair. We were deep in a Product Showcase with thousands of non-human identities (NHIs) scattered across AWS, GCP, and other platforms when the Token Security platform surfaced something suspicious.
Employees were using an AWS Access Key which was unrotated for over 4 years tied to IAM User with AmazonS3FullAccess and CloudWatchFullAccess.
What we noticed were:
- No Virtual Private Cloud (VPC) endpoint policies!
- No IP restrictions!
- Wide open!
For most people outside the security team, that might not sound like an immediate crisis. But for anyone who’s been on an incident bridge call at 2am, you know exactly why our pulse quickened.
This key was effectively an all-access pass that could be used from anywhere in the world to all their S3 Buckets.
Why This Is Dangerous
This account wasn’t just some low-privilege placeholder. It was a core user, created years ago, still active, and used for legitimate automation tasks.
But, here’s the problem:
- The key hadn’t been rotated since creation
- It was originally set up by a developer who’d left the company
- It had access to all S3 Buckets in AWS.
No IP restrictions meant that if the key leaked through code commits, logs, or some malicious activity, it could be used from any device, any network, any country.
And, with long-lived credentials, time is on the attacker’s side to exfiltrate all company data from S3 within minutes or plant persistence by modifying CloudWatch alarms.
How We Handle It: Proactive and Reactive Defenses
At Token Security, we break down our IP Hardening approach into two modes:
1. Proactive Posture Management
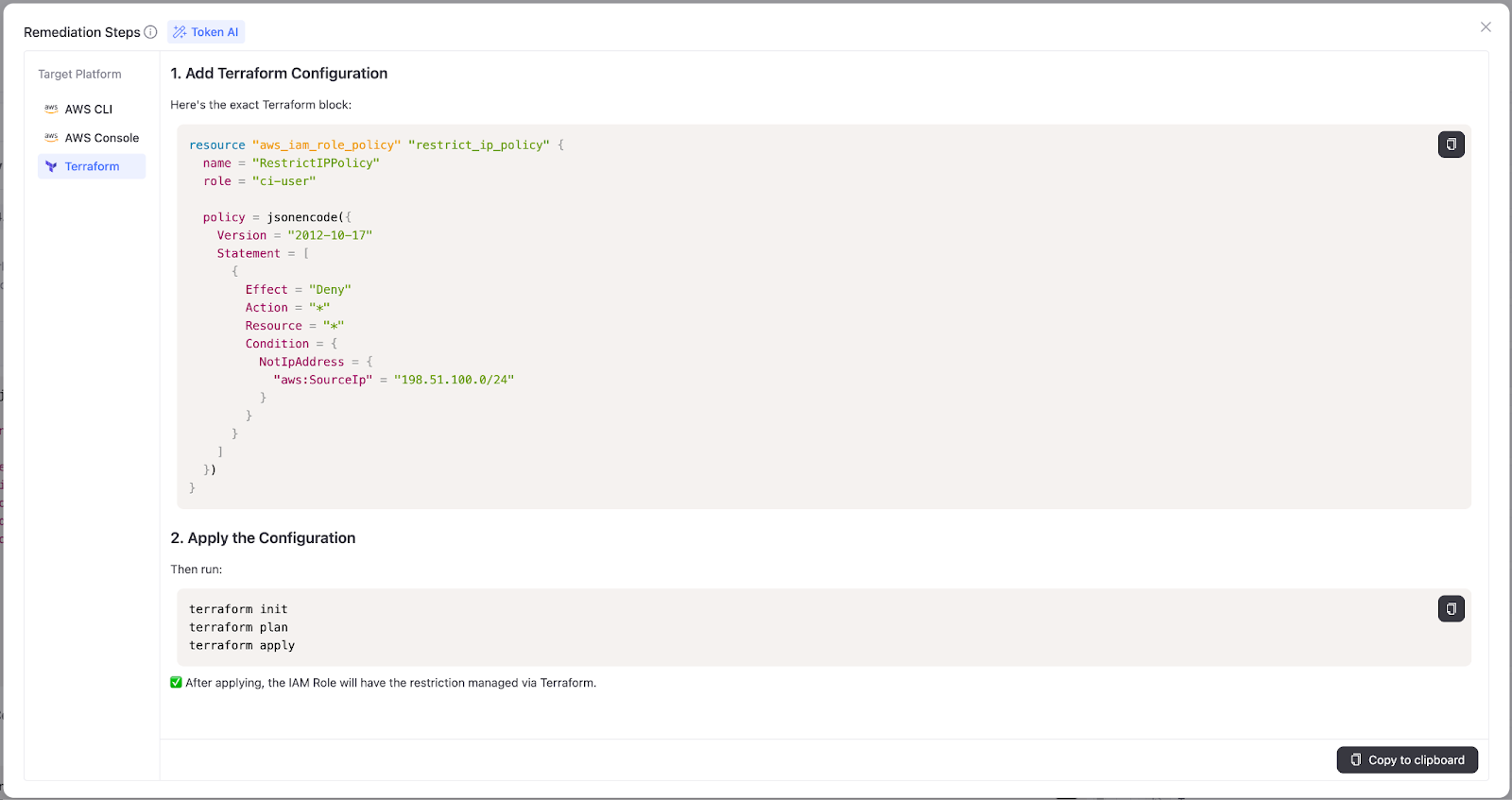
As soon as our Security Posture Management engine detects a Missing Network Policy on an NHI, we flag it and can generate a Terraform remediation script.
That Terraform script can:
- Lock the identity to a list of trusted corporate IPs
- Restrict it to VPN ranges
- Block all but explicitly approved network origins
If the customer is ready to fix it immediately, they can apply the policy in minutes with no manual digging through console menus and no guesswork.
2. Reactive Protection via ITDR
Sometimes you can’t apply IP restrictions right away. Ownership might be unclear, the change might require downtime, or the account might be tied into too many workflows to alter it instantly.
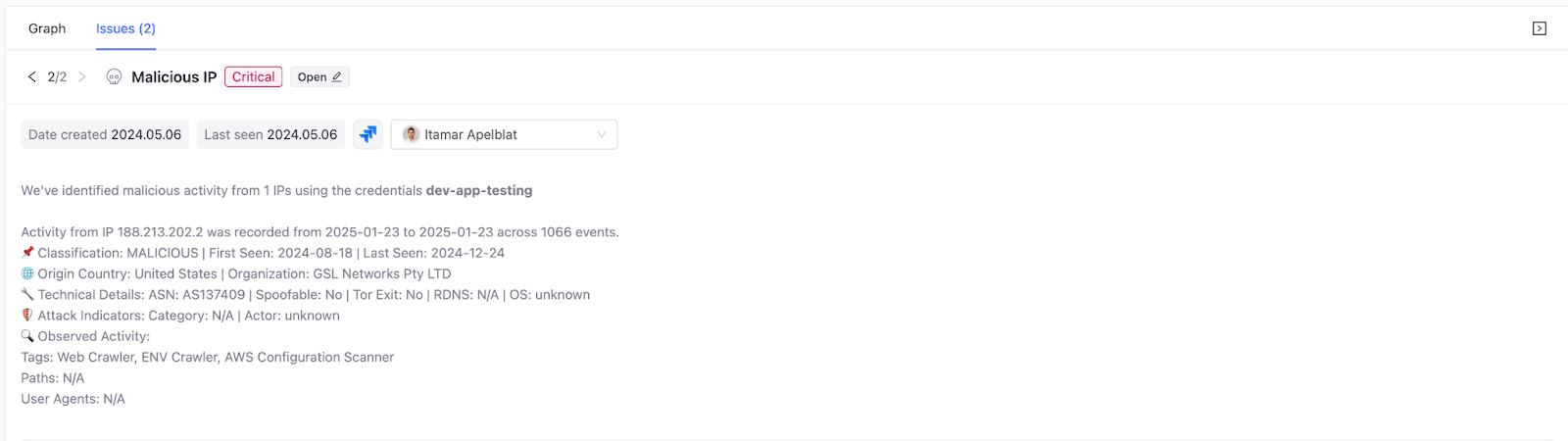
That’s where our Identity Threat Detection & Response (ITDR) capabilities comes in. We enable our customers to continuously monitor that NHI for abnormal IP activity:
- Cross-checking against threat intelligence from sources like GreyNoise and Criminal IP
- Detecting connections from known malicious IP ranges
- Alerting instantly and providing the same Terraform script as discussed above, now as an emergency measure
Even if proactive hardening isn’t possible today, we make sure you’re ready to react the moment something goes wrong.
The “What If” That Keeps You Up at Night
Imagine this scenario:
An attacker gets access to the AWS Access Key. They connect from an overseas IP flagged for botnet activity. Without IP restrictions, they can run wild, reading and deleting data, altering configurations, and pivoting into other environments.
In the scenario we highlighted above, the story went differently. The Token Security platform flagged the exposure before it was exploited. The team at the organization evaluating our solution applied the Terraform IP restriction, and the account was locked down to corporate VPN addresses.
Why the Token Security Platform Works to Keep You Secure
- Shrinks the Attack Surface: IP restrictions cut off the vast majority of abuse scenarios
- Complements Key Rotation: Even if you miss a rotation window, hardened IP rules protect you
- Bridges Gaps: ITDR monitoring covers the lag between discovery and remediation
- Automates the Fix: The Terraform script means no “we’ll get to it next sprint.” It’s ready to deploy now
Key Takeaways
If you’re serious about NHI security, IP Hardening isn’t optional. It’s a low-effort, high-impact control that turns a wide-open door into a narrow, guarded checkpoint. And, when paired with continuous monitoring, you’re not just building a better wall, you’re watching it, day and night.
IP Hardening should be a standard part of NHI security hygiene, especially for identities with persistent access keys. Token Security’s approach blends proactive security posture management with real-time incident detection, ensuring that if you can’t remediate immediately, you can still defend effectively.
If you’d like to see how we identify and secure NHIs with missing network policies in your environment, request a demo and we’ll show you how we can help you close this gap in minutes.
.gif)






