The Machine Identity Crisis: Navigating Uncharted Waters in Cloud Identity Security
.avif)
In the realm of cybersecurity, a profound revolution is underway towards a comprehensive cloud-native infrastructure and workforce. For CISOs at the helm of cloud-native companies, this shift brings new challenges, particularly in the domain of securing identities.
In this blog, we'll explore some of the lesser-discussed yet critical aspects that have pushed our identity management challenges to the brink.
We are Mismanaging our Identities
Mismanagement of identity, access, or privileges contributed to 75% of security breaches, such as the 2024 Microsoft breach, Cloudflare 2023 Thanksgiving breach , the MGM resorts 2023 breach and many more.
Securing identities can be a real challenge these days. With the constant evolution of attackers' tactics and the increasing complexity of business operations, it's no wonder why achieving a perfect level of identity security is so tough.
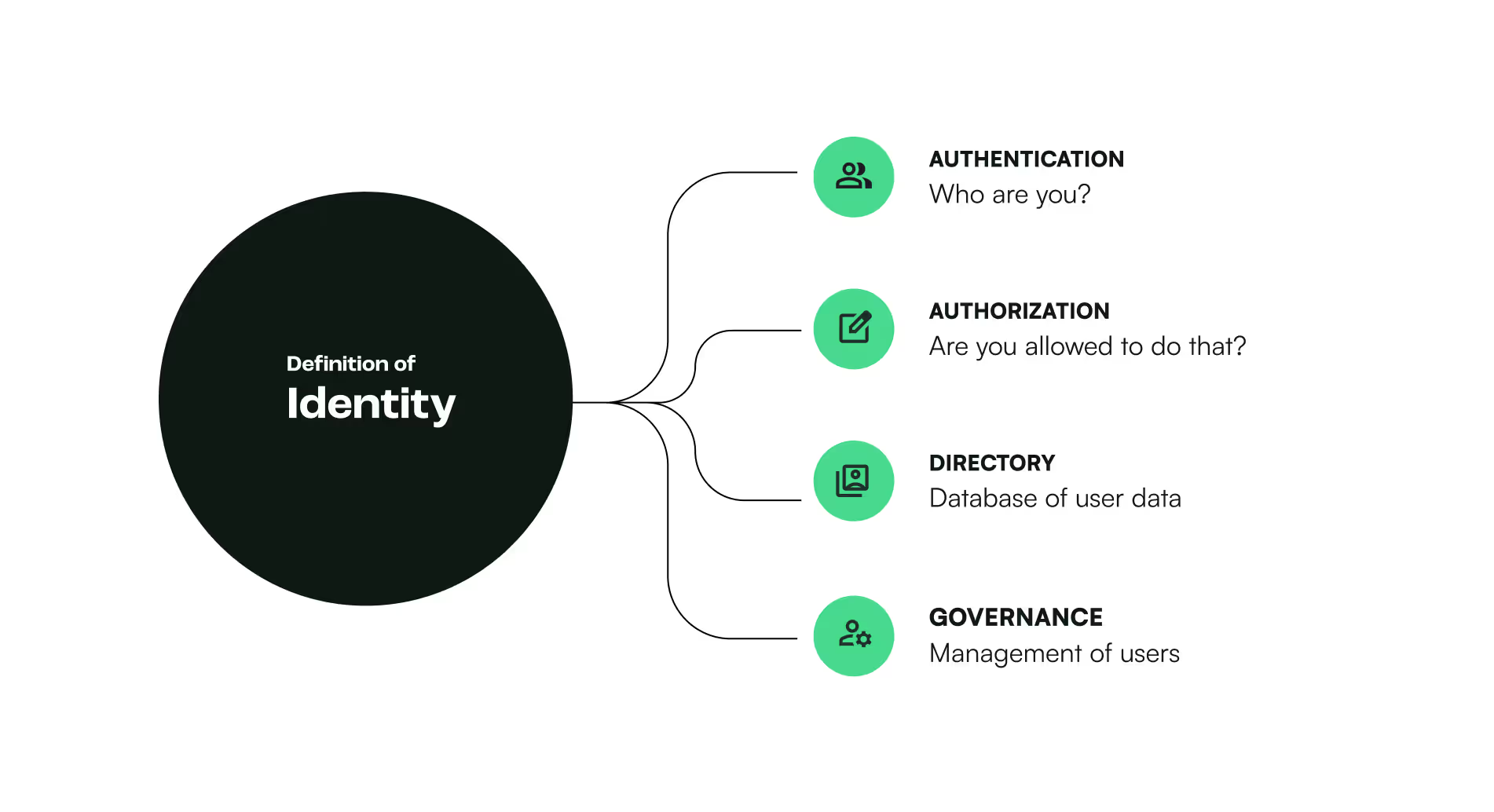
Organizations typically concentrate on two key areas of identity security: (1) authentication, which confirms a user’s identity, and (2) authorization, which assesses whether a user is permitted to carry out certain activities. Nevertheless, numerous crucial factors often result in the collapse of these protections.
Let's start by examining how traditional security boundaries have shifted.
The network perimeter erosion
Traditional perimeter defenses like firewalls, VPNs and proxies today are both inadequate and obsolete in organizations built on IaaS and SaaS.
If you can’t trust the messages you’re getting by their network source, you have to trust the identity sending them. That means you have to figure out who that person/machine is, why they’re trying to interact with you, and whether or not you should open that message.
As more and more of companies’ assets continue to move outside the firewall, policies like Bring your Own Device (BYOD) emerged. This accelerated the building of new categories like mobile device management (MDM), machine and workload identity, and more.
Shattering of AD to multiple cloud-based directories
Historically, Microsoft’s Active Directory (AD) served as the centralized repository for managing user and machine identities. Now, the use of Active Directory has become a source of frustration. AD integrations were a hassle - they were so fragile! Managing AD became this never-ending task for whole teams of IT admins. Plus, it wasn't exactly a walk in the park to incorporate non-Microsoft apps and devices into the mix.
It would take days to grant a new user access to an app, sometimes even weeks! No wonder business users started feeling frustrated with IT, seeing them as a roadblock to their own productivity.
Currently, almost half of organizations manage their identity and access rights using over 25 different systems, as highlighted in a recent study conducted by OneIdentity.
As businesses expand, merge, and undergo frequent restructuring—with middle managers competing for power and reorganizing multiple times in a quarter—the complexity of identity management grows. This is compounded by decentralized purchasing of cloud environments and identity providers driven by bottom-up adoption. This complexity is evident in managing database users, Kubernetes cluster RBAC, and API keys for SaaS, among other areas.
Transitioning from Microsoft AD is challenging due to its deep integration in enterprise systems. It's not just a technical hurdle, but a significant operational shift. The widespread use of AD and its complex ecosystem make migrations lengthy and potentially disruptive, requiring integration of non-Microsoft products, adoption of new technologies, and staff retraining.
Legacy Systems in a Cloud-First World
Some of the most valuable standalone identity companies in the market are Okta, CyberArk, Delinea, Ping Identity, and ForgeRock. All of them were founded prior to 2010.
These companies only cover a portion of the problem and primarily support on-prem infrastructure, leaving a large attack surface for cloud-first companies driven by the rise in machine identities. It would be very complex for them to handle the dynamic nature of cloud services, especially when it comes to managing machine identities that require rapid provisioning, scaling, and revocation.
If you chat with most enterprise IT professionals, they'll let you know that shifting users from an older on-premises setup to a brand new cloud deployment, even if they're supposed to be identical, is no walk in the park.
Unfortunately, this approach often comes up short. On-premises identity solutions just don't seamlessly transition to cloud environments, which operate with different dynamics for access and authentication. As a result, outdated identity measures struggle to adequately safeguard modern cloud-based resources, leading to inefficiencies and increased risks.
It's clear that we need a lot of innovation to address this problem!
Multi-Account and Microservices Architecture
Every account can potentially become a privileged account depending on the circumstances.
The emergence of microservices and the widespread implementation of Infrastructure as Code (IaC) have resulted in a complex multi-account architecture that adds another layer of intricacy to identity management. Each individual microservice or cloud resource may have its own unique identity parameters.
For instance, when an engineer wants to launch new instances in AWS, they require special privileges to do so. Essentially, any user who needs access to the cloud infrastructure becomes a privileged user.
A staggering 99% of users, roles, and services are given excessive permissions. This high level of privilege allocation poses significant challenges.
Without a dedicated solution in place, managing this complexity can lead to configuration errors and overlook potential security risks, ultimately leaving the system more vulnerable than ever.
How Token Security Can Help
At Token Security, we have devoted significant time and effort to gaining an in-depth understanding of these challenges.
Our solutions are designed specifically for cloud environments, helping security teams secure their machine identities with precision and agility with a machine-first approach. By providing tools that monitor and manage the attack surface of both user and machine identities—including IAM users, access keys, and API keys—Token Security empowers organizations to maintain robust security standards in the cloud, seamlessly and effectively.
As the cloud continues to redefine the technological landscape, the need for robust, cloud-native identity security solutions becomes increasingly critical. For companies poised on the brink of innovation, understanding and adapting to these challenges is not just an option—it’s a necessity for safeguarding their future.
Stay tuned for more insights and join us on this exciting journey to a more secure digital world. Together, let's innovate and transform challenges into opportunities for growth and security!
.gif)






